As we enter the 2020 election season, we are once again discussing the possibility of foreign intervention, which puts the 2016 hack of the Democratic National Committee back in the news. It seems that there is more confusion now than when it happened. But the hack was fairly straight forward — you didn’t need to be a US Intelligence officer to understand what happened. (In fact, we hosted a webinar covering what the industry knew about the attacks.)
Here are five things we know about the attack that seem to have been forgotten in the last three years.
1. There Is No Server
The Democratic National Committee hosted their email in Google G Suite, which is entirely cloud-based. As is the nature of the cloud, their emails were spread out amongst several Google data centers and, frankly, it would be impossible to point to a single physical device containing all the DNC email accounts.
2. No Really, It Was the Russians
Despite confusion in the news on whether the attacks were Russian or Ukrainian-borne, the matter has been settled for three years now. When it happened, the DNC hired security firm CrowdStrike to stop the attack, prevent further leaks, and isolate the source of the breach. The FBI confirmed CrowdStrike’s conclusions, and five politically-independent cybersecurity firms who had access to the same information corroborated this.
Each firm concluded that two Russian groups were responsible for the attack. They had been found responsible for earlier attacks in the US, Germany, and the UK. While each firm might have given them different code-names, the conclusion that Cozy Bear and Fancy Bear were responsible is set in stone.
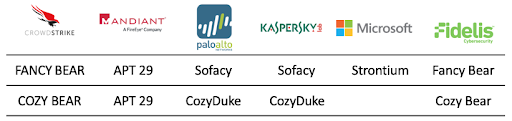
Fancy Bear is a well-known “Advanced Persistent Threat” tied directly to Russia’s military intelligence agency, the GRU. Because they were implicated in previous attacks on the White House, the State Department, and the US Joint Chiefs of Staff, they’ve been actively monitored by most every security organization — both public and private.
Cozy Bear is a separate organization tied to the FSB (formerly known as the KGB) that is monitored by the FBI, CIA, and NSA. A year before the 2016 attack, in the summer of 2015, the FBI warned a number of organizations, including the DNC, to monitor their networks for suspicious traffic from an ongoing Cozy Bear attack.
3. The Evidence Is Clear
One benefit of hosting email within Google’s servers is that their infrastructure maintains a tremendous amount of forensic data forever. The 2016 attack was traced back to individual phishing email messages that, even today, can be analyzed by anyone with access, including investigators in both the US Executive and Legislative branches of government. At the time, the emails were shared with CrowdStrike and the FBI for further investigation.
To fool DNC employees into sharing their Gmail credentials, Fancy Bear hackers sent 3,907 emails from a spoof of their outsourced IT company “misdepatrment.com” to addresses at the DNC and the Hillary Clinton campaign telling them they need to change their passwords. Some used “actblues.com”, a spoof of the Democratic fundraising site Act Blue.
This was an extremely targeted attack. Each of the messages included a unique bit.ly link that encoded both the attackers’ server as well as the victims’ name and email address. While the bit.ly links have since been taken down, they were publicly available for months after the attack. For example,
This link would redirect a user to an extremely accurate mirror of Google’s login screen, complete with the victim’s information filled in, matching what they would see on a legitimate page.
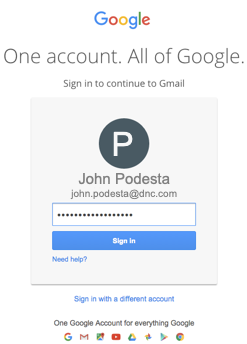
All of these links and IP addresses were tied to Fancy Bear long before the attack.
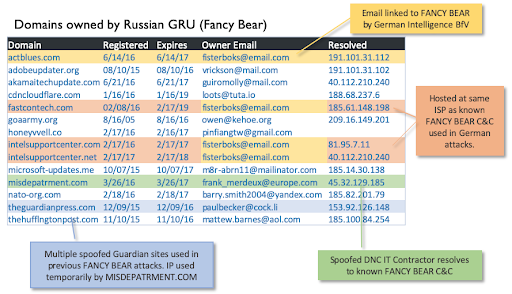
This very clear digital trail was just one of many clues. The 2016 Russian attack against the DNC has been unanimously confirmed by all 17 U.S. intelligence agencies, the Mueller report, and the Republican-led Senate Intelligence Committee. There is no debate.
4. The Russians Blamed Romania Before Ukraine
As news of the attack came out in the press, a Romainian hacker known as Guccifer 2.0 immediately claimed responsibility. Communicating through a French AOL account, he sent journalists “proof” that he was acting alone, but his credibility dissolved fairly quickly. Not only was he logging into his email account via a Russian-hosted VPN, all of his documents had been created on a Russian version of Microsoft Word. When interviewed by Romanian-speaking journalists, he struggled to carry on extended conversations in his “native” Romanian tongue.
Last year, Special Counsel Robert Mueller’s office named Guccifer 2.0 as a Russian intelligence officer and indicted him along with 11 other GRU operatives.
Since 2017, there has been a concerted effort to pin the attack on the Ukraine. They have been fortunate to have deployed this tactic at a time in which social media holds greater sway than forensic data, but just as in the Guccifer 2.0 case, most every source of this theory can be traced to Moscow. As early as 2016, the idea was being promoted by Konstantin Kilimnik, who was born in Soviet-era Ukraine and attended a Moscow academy run by the GRU before working for Oleg Deripaska, a Russian oligarch and Putin ally.
5. CrowdStrike Is Not Ukrainian
CrowdStrike is a well-known, publicly traded, provider of endpoint security, based in Sunnyvale, California. They were famously mentioned by President Trump as being tied to Ukraine, which is inaccurate. Their relation to the attack is due to the DNC leveraging their services after the breach.

Conclusion
Politics and cybersecurity are murky topics, often fraught with misinformation, which is why they are both so often debated. However, that does not mean that there isn’t a basis of fact for both. Looking back at our webinar from that year, we can see that long before the source of the DNC attack became a political issue, none of the forensic details were in dispute.
We hope this review of that webinar offers some clarity around those facts. Hundreds of industry and government research professionals invested long hours to uncover the truth. Their conclusions can be helpful as long as they are not ignored.
*Avanan is neither affiliated with, nor endorses, any political party or candidate.







