In the past 30 days, the Avanan platform has detected and blocked thousands of unique phishing attacks against our customers. The most interesting are those that bypass the built-in Office 365 and Gmail filters. In this blog we discuss the five most common phishing attacks we detected and blocked that bypassed Microsoft’s and Google native security.
We hope that by putting the spotlight on phishing emails that are not detected by Google and Microsoft we can help organizations that are not using our security software. Sharing this report with your employees may prevent them from falling for one of these common schemes.
The attacks of the last 30 days ranged in sophistication from typo-riddled “Nigerian Prince” scams to sophisticated forgeries of reputable landing pages that would fool even the most diligent of employees. Rather than show all of them, we thought it would be more helpful to list only the top five in terms of execution, as those are the easiest to miss.
Google and Microsoft couldn’t recognize these emails as malicious, could you?
1. DocuSign: Document share
This month we saw a dramatic increase in the “DocuSign” attacks. The email looks identical to a signing request from DocuSign, even purporting to come 'via DocuSign', but it is not coming from a spoofed sender. Clicking the link either takes you to a fake authentication screen or in some cases, triggers a malware file download.
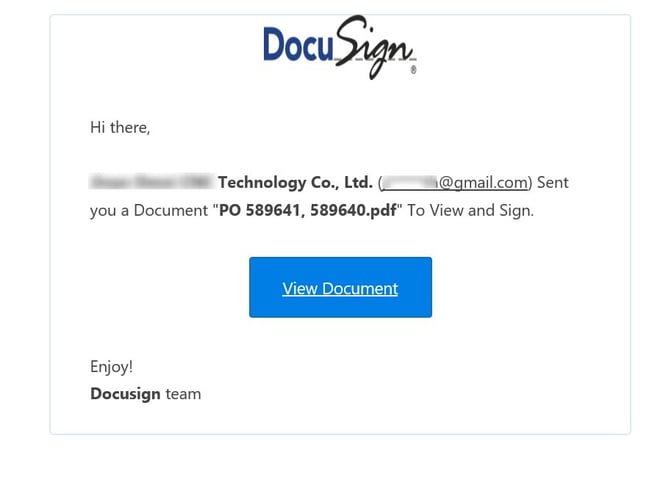
How we caught it: The Avanan platform flags these attacks as “Brand Impersonation” - Emails that visually mimic a branded company but are not coming from that sender.
Avanan offers a free scan of all your inboxes to detect which phishing attacks got through to your users.
2. Office 365: Login page
Like in previous months, many of the attacks this month included a link that looks like an Office 365 login page in an attempt to harvest the end-user’s credentials. The email content copies a legitimate file-share or other sharing event, and therefore the end-user does not see anything unique when requested to login.
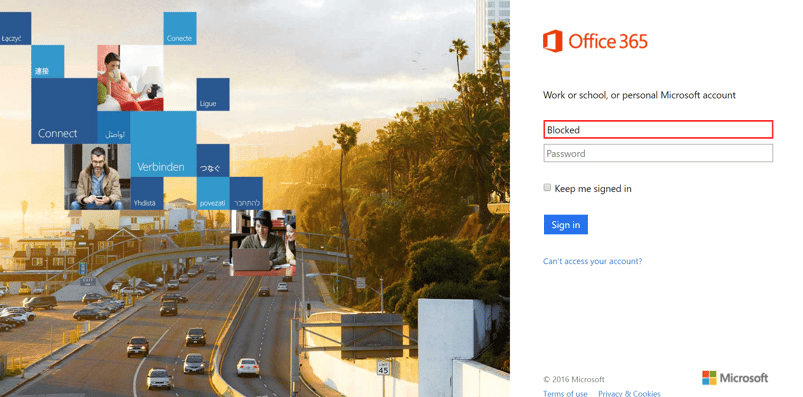
How we caught it: Avanan detected these attacks through our malicious URL detection tools. These tools have two components - the first is URL filtering of known attacks, leveraging several feeds from multiple vendors. The second and more important one, is emulating the page to detect zero-day/unknown URLs. The following document explains this technology in detail: Secure Your SaaS from Malicious Links (White Paper)
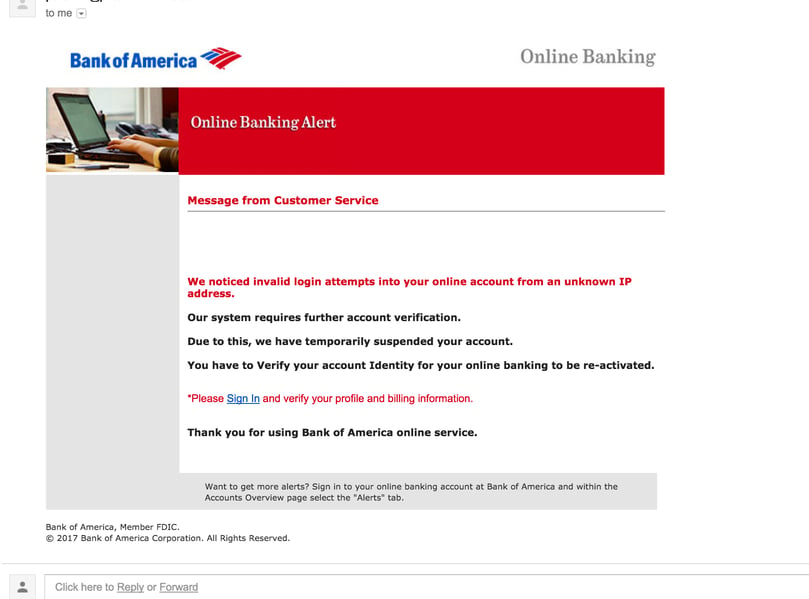
3. Bank of America: Invalid login attempts
A seemingly helpful warning from Bank of America that will capture your banking login username and password giving the hackers full access to your finances.
4. Netflix: Update payment method
A new comer to the top-5 billboard this month was a ‘brand impersonation’ of Netflix. In this request, the end-user is asked to update their payment info for their Netflix account. The flow is identical to the Netflix flow, at the end of which the hackers have your credit card information, and also can watch Netflix video with your account. If Netflix starts recommending awkward content, your account may have been hacked ;-)
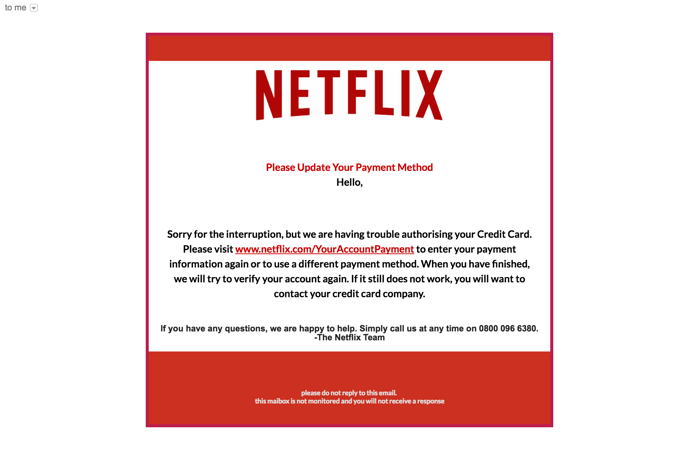
How we caught it: This attack was detected by Avanan as “Brand impersonation” (Email from “Netflix” coming from another account).
5. Fidelity: Unrecognized device login
Similar in nature to the Bank of America account, this month saw high usage of “Fidelity” for phishing. Although it may look like Fidelity is informing you of potential fraud on your account, the only risks you are facing lays on the other side of the links contained in this message.
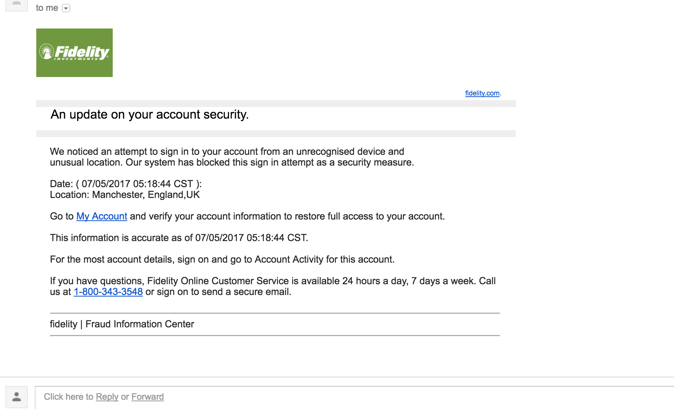
How we caught it: The Avanan platform flagged it as both “brand impersonation” and malicious URL emulation.
Conclusion (and good news!)
While Microsoft and Google are doing their best to block these attacks, the hackers have free access to their best security and are constantly experimenting with it until they find a way in. The Avanan platform allows you to select any security from the top vendors in the market, and implement as simply as install an app on your account. It’s all cloud based, no rerouting of traffic (Like an MTA) and nothing on the endpoint.
If you are already using Avanan, you won’t have seen any of these emails and neither have your employees. Every email our customers receive is scanned, analyzed, and tested before it reaches the end-user. Avanan’s anti-phishing bundle include impersonation analysis, URL and File analysis, and AI baselining to detect suspicious emails. Depending on the policy, Avanan will either quarantine the email or warn the end user of the phishing attack. It acts only after the built in security of the service - what Microsoft and Google put in place - completes its scan, giving you real multi-layer security.
If you are interested in learning more about how Avanan can protect your organization from phishing attacks click here to set up a demo and one of our security experts will contact you for a personalized walk through.






