A fairly basic attack has stolen thousands of accounts across major organizations.
Dubbed "0ktapus", this campaign started by using a phishing toolkit. The hacker would use the toolkit to send an SMS phishing message to the intended recipients. These looked just like the typical authentication pages provided by the company. End users enter their credentials, and now the hacker has carte blanche to enter the organization's back-end.
As Group-IB reports, the URLs of the phishing sites are designed to look convincing:
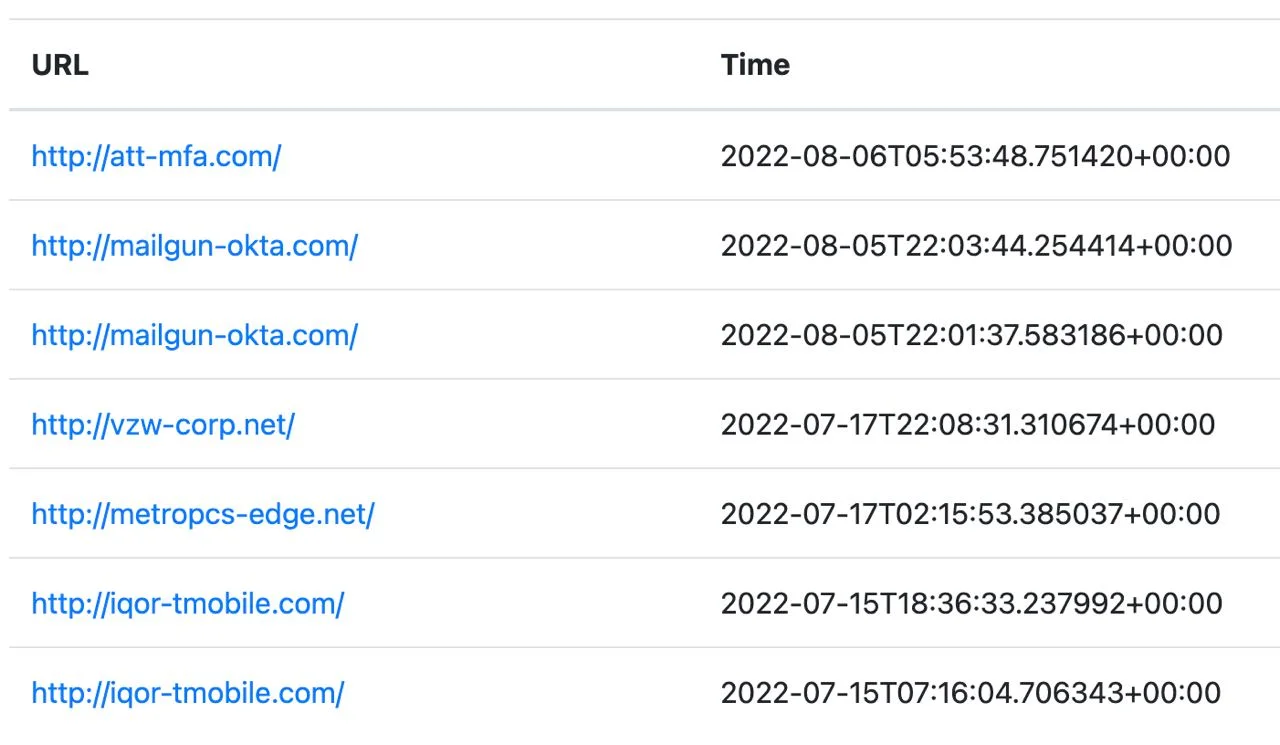
Those aren't legitimate links, but you'll see how they spoof cellular brands like AT&T or Verizon. That lends legitimacy to a user looking at the URL.
The group also started the campaign via an email or through stolen MFA.
When a bad guy has an email and a phone number, they can use it for MFA spoofing, or other vishing or "Smishing" scams, which utilizes text messaging. (That's why we recommend removing your phone number from all accounts and never using it for MFA.)
Implementing MFA is great, and an essential step for all companies. Relying solely on it? Not so much. MFA does not solve the phishing problem. Attacks can automate the login to happen at the same time as capturing their own login. Instead of authenticating a login, users are essentially approving the attacker's attempts to infiltrate the system. That's why we've implemented an MFA anomalies engine, which detects login operations that failed the MFA stage.
With advanced phishing protections in place, the organization would be able to monitor suspicious logins, and suss out phishing URLs at click time, especially those that detonate post-delivery. Plus, User and Entity Behavior Analytics plays a key part. UEBA predicts if a user has been already compromised, by observing login trends, email habits, and the browser environments that the recipient uses. UEBA monitors the typical behavior of users so that when something out of the ordinary happens, it will stand out.
Key aspects of UEBA include an understanding of user login locations (e.g., log-ins from locations too geographically distant as to be reasonable in a short period of time, often called a “Superman Attack”), suspicious mail-forwarding rules (like forwarding all mail to an external account), user activity aberrations (e.g. a user who normally sends 50 emails per day all of the sudden sending 500 in one day), and detecting the version of a browser someone is running in case an outdated version has known security holes leading to data leakage.
This is particularly critical if you are using a Legacy Email Gateway. These gateways sit in front of the inbox; however, by their architecture, they disable Google or Microsoft's protections. And since UEBA actions only help post-delivery, if a gateway's non-UEBA misses a phish--which it often does--it will go straight into the inbox.
It is incredibly easy for anyone to download a phishing kit and begin using it. The perpetrator doesn't even have to be incredibly technically savvy. (Indeed, Group-IB thinks that even though the attack was quite successful, the threat actor remained inexperienced. That speaks to the power of these phishing kits.)
Without proper protections in place, a simple phishing kit can do a world of damage.