Soda PDF is a popular PDF editing tool. It allows for the easy editing of PDFs–which is not always an easy thing to do–as well as various features like conversion to different formats, and e-signature services.
It is a trusted, legitimate service. And as we’ve seen so many times with BEC 3.0 attacks, legitimate services are ripe for exploitation. It provides hackers a way to latch on to the legitimate service and get into the inbox.
In this Attack Brief, Check Point Harmony Email researchers will discuss how hackers are sending messages directly from Soda PDF, using its legitimate service to send emails that encourage users to call a phone number, where money will be attempted to be stolen.
Attack
In this attack, hackers are using legitimate PDF services to send malicious activities.
- Vector: Email
- Type: BEC 3.0
- Techniques: Social Engineering, Impersonation, Credential Harvesting
- Target: Any end-user
Email Example
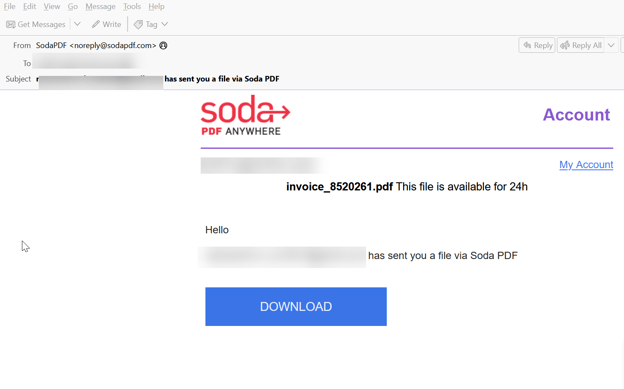
This email is sent directly via Soda PDF. It’s sent as an invoice, with a download link that goes directly to Soda PDF.
The page has been taken down, and eagle-eyed users will note that the email says that the PDF will expire within 24 hours. But the page goes to a GeekSquad look-a-like invoice. There’s a phone number that the invoice asks you to call if you think there’s been an error.
When you call that number, you’ll talk to a human, but it’s the second part of the scam. In order to cancel the order, they’ll ask for your credit card information. Of course, that’s where it’ll be stolen. Even if you realize what’s going on before handing over your credit card details, the scam isn’t done. They now have your phone number, to target you with further scams via voicemail, WhatsApp and text.
Techniques
This attack combines two things that we’ve talked about often. BEC 3.0 and phone number harvesting.
BEC 3.0 is when hackers leverage legitimate services to send out malicious material. That could be anything from an invoice from QuickBooks or a document on Google.
The second is phone number harvesting. By encouraging the end-user to call, the hackers are able to obtain your phone number. Now they have your email and phone number. With the number, they can carry out even more attacks, utilizing text messaging, voice mail and WhatsApp.
These attacks can be incredibly difficult to stop and spot. BEC 3.0 presents tremendous challenges. Websites like Soda PDF are legitimate and then there is nothing wrong with them.
What happens, though, is that the ability to enter content that leads to malicious activity comes into play. On these sites, people can create anything–invoices, documents, etc., all including either malicious redirects or instructions for a phone call. These attacks leverage the legitimacy of these sites to get into the inbox.
From there, it’s up to how convincing the context of the email is to encourage the person to click or call.
Traditional AI techniques like Natural Language Processing may not be as effective. There’s nothing inherently off about the language since it comes from a legitimate source. One of the only ways to stop this attack is by scanning the page for phone numbers with AI. AI is able to scan the phone number to see if it’s legitimate or if it’s been associated with a scam.
These attacks are starting to catch on. As they proliferate, more education o the half of users and more sophisticated tools from providers will be needed.
Check Point Harmony Email researchers reached out to Soda PDF on June 8 to inform them of this attack and research
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that looks at all URLs and emulates the page behind it
- Leverage URL protection that uses phishing techniques like this one as an indicator of an attack
- Utilize advanced AI to scan phone numbers






