In December, Avanan researchers discovered a new phishing attack that involves sending a plain text email with malformed URLs to bypass the URL protection and rewriting features of email security solutions. We named this method the SLINKIFY attack.
Avanan and Check Point provide complete protection, while Microsoft Defender and Proofpoint allow the end-user to receive the email and potentially click on the malicious link. Because the links have not been rewritten, the user goes directly to the phishing site.
Check Point Researchers, over a month since the initial release of the report, have re-created the attack, this time specifically against Microsoft Defender.
Here's how it works in action.
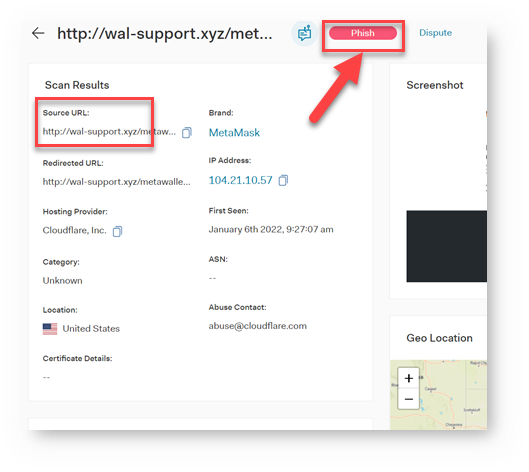
Step 1: The Verified Phishing Link
For this attack to be worthwhile to hackers, the phishing link has to be verified and actually work. In this case, the link is certainly phishing:
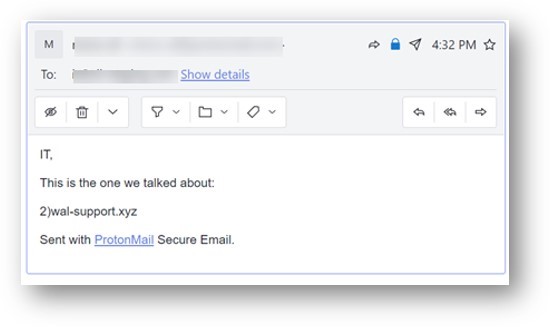
Step 2: Sending an email
The email is sent to a Microsoft-protected address. As discussed in the original research, it uses a malformed link. That includes "gluing" a non-alphanumeric character to the URL. (In this case, it's a parenthesis.) This confuses the scanner into thinking there is no URL at all.
Step 3: Microsoft Can't Identify the Link
Because the link is malformed, Microsoft doesn't identify it as malicious. This leaves users exposed.
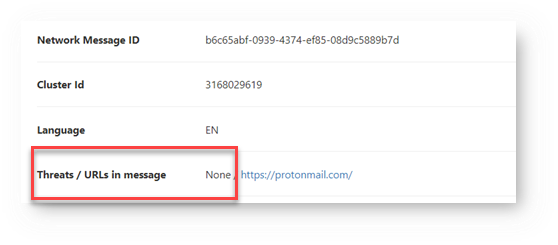
Step 4: The User is Directed to Phishing Link
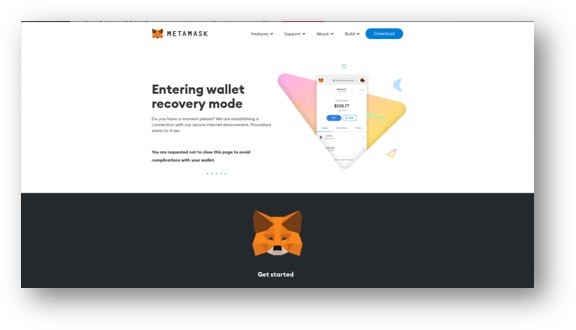
Since the URL wasn't rewritten, when the user clicks, they go straight to a phishing site:
How Avanan and Harmony Protect Against This Method
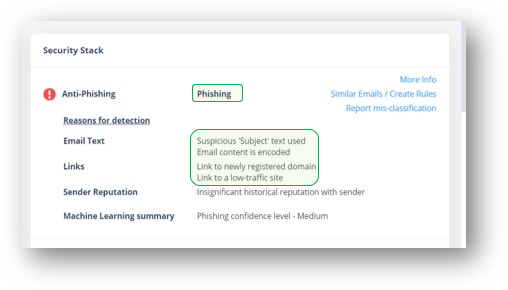
Avanan takes a holistic approach. By noticing that there's a suspicious subject, and encoded email content, as well as links to low-traffic sites and insignificant historical reputation sender, we know this is phishing and block it.