Threat actors have long taken advantage of current events -- from natural disasters to regional holidays and cultural moments -- to deceive people.
This week, Harmony Email & Collaboration researchers found over 15,000 examples of a burgeoning attack that looks to take advantage of the current situation in Israel and Gaza. These emails, aimed at a variety of industries and organizations around the world, have links that contain “israelvspalistine,” along with an HTML attachment.
The emails are disguised as a donation confirmation notice, either with or without an attachment.
Below, see three separate, albeit similar emails. The subject line is generally the same. Some have an HTML attachment visible, some do not. Some are sent via a mobile device, some are not. There is one that is sent in Spanish as well.
Example #1:

Example #2:
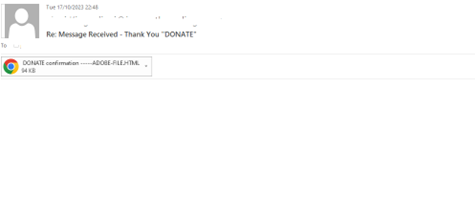
Example #3:

Whether the HTML attachment is shown or not, it doesn’t mean it’s not there. Sometimes it’s obfuscated by code; other times it’s not. In all the above cases, the email directs the end-user to the attachment below.
The HTML attachment is named ADOBE-FILE.
HTML files are one of the most common attack vectors. According to Check Point, more than 50% of malicious attachments are HTML or HTM files, by far the top vector for malicious URLs or attachments.
In this case, users are redirected via the HTML attachment to the following spreadsheet.

This HTML file, disguised as an Excel file, requires the entering of email and password. This will lead to stolen credentials.
As the war continues, we expect to see more email-based attacks aimed around these topics. In the beginning of the war, we saw a 52% increase in cyberattacks on the government and military sector in Israel, along with an 18% general increase.
Harmony Email & Collaboration users remain protected from this attack.





