Credential harvesting remains the most popular form of phishing.
Even though these attacks can seem simple to spot, there's a reason they are so popular--they work.
Why? Because these attacks seem urgent (password reset, claim gift now) and often look fairly convincing.
This attack plays on the urgency factor. It showcases a "high extremity" alert (although that grammar is odd) and notes that a password is about to expire, the same day as the email is sent.
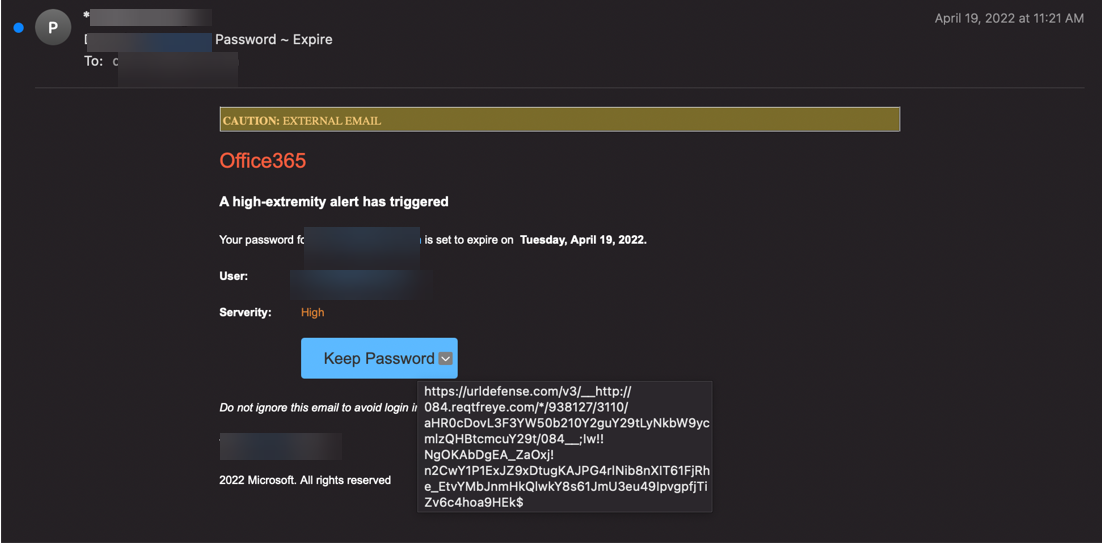
This plays on the urgency factor. It even says, "Do not ignore this email".
On analysis, however, the sender address does not match, there's missing DMARC, and an insignificant historical reputation with the sender.
The URL, as you can see, goes to URLDefense, which is Proofpoint's link rewriting feature (although the legitimate site would be urldefense.proofpoint.com). That is a clever additional feature of this attack. Whether you use Proofpoint or not (and the recipient in this case does), everyone has likely seen that URLDefense tag. It gives a veneer of legitimacy and of comfort. It also allows hackers to target their attacks to Proofpoint customers, since that can be found via public records.