Slack is rolling out a new feature that will increase collaboration, but also increase hacking activity.
Called Slack Connect, the feature allows you to DM anyone at any company. Want to start chatting with a CEO at your dream company? Go for it!
The new feature works by sending a special link to anyone. (It's similar to sending a DM request to someone who doesn't follow you on Twitter.) In some cases, but not all, it may require Slack admins to approve it.
There are two ways to look at this. One, it will undoubtedly increase collaboration and communication with partners and companies. And it can be used as a sort of social network with friends from other companies.
But here's the second way to look at it: This may be the start of open season for hackers. Your Slack Security could be at risk.
Remember, even before this new feature, it was relatively easy for external members to join a company's channel. Any user, at almost any permission level, can invite others to join whether inside or outside the company. The approval process is often loose and casually enforced. Now, it will be easy for hackers to do a simple account takeover and start "Connecting" with users at tons of companies and begin sending malware. Remember, there is no inherent protection against malicious links or malware within the Slack platform.
Even worse: profiles are just indicators of identity and can easily be edited. Often done as an internal joke, with this new feature, it can have devastating consequences.
Consider this example:
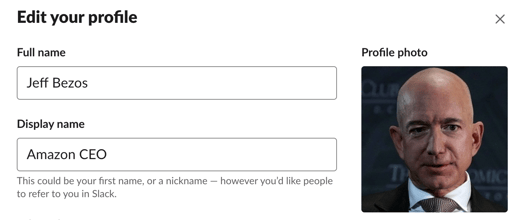
Maybe someone isn't impersonating Jeff Bezos--but you can see how easily it can be done and how it can easily fool someone on the other side.
With more external users joining the fray, a lot of chaos can ensue:
- One-click forwarding of sensitive information outside the organization, either by mistake or deliberately
- External members, who can easily join a company's channel, are free to access an entire repository of information
Any data or information shared on Slack can easily be passed on. This can happen maliciously or by mistake—many users consider Slack to be internal but forget that external partners might also have joined a channel.
Then, of course, there's the potential for East-West attacks.
The first compromised account typically happens by email. Subsequent 'east-west' compromises typically avoid email in order to avoid detection. As companies continue to hold tons of internal communication on Slack, the attackers will follow.
With this new feature, it will become incredibly simple for outside, bad actors to access entire Slack channels and send malware or malicious links and access an incredible amount of sensitive information. It was easy before. Now it could become a walk in the park for hackers.
This sounds daunting. It doesn't have to be. The Avanan solution remains the gold-standard:
- Every file is sandboxed before downloading. When zero-day malware or ransomware is discovered, Avanan quarantines the file, performs threat extraction, and alerts the user, who has the option to request file restoration.
- DLP security tools detect leaks of PCI, HIPAA, FERPA, PII, and other sensitive information. When necessary, Avanan adds a -classified suffix to the end of confidential messages or files. Flexible workflows determine if the content is quarantined, the user is alerted, and/or the file is encrypted with IRM.
- The anomaly engine monitors all Slack logins and events for suspicious activity. Avanan alerts the Slack administrator, the affected accounts, and disables the compromised account to prevent the spread of sensitive data, malicious files, and phishing URLs.
- A detailed dashboard updates administrators on general usage in Slack. The Avanan Slackbot logs the total number of users, files, shares, links, logins, channels, and threat detections.
You can add Slack Connect and still get the same security features you've come to expect from Avanan.
Not a bad one-two punch.