We’ve been talking about it week after week—hackers are using legitimate services for illegitimate means.
Why is this increasing in popularity? It’s easy. Just sign up for any popular SaaS tool. It’s free. And the hackers are able to send it out with the legitimacy and reputation of these brands, making it nearly impossible for security services and end-users to decipher.
We continue to see new services used. This is not an issue with the services themselves. Rather, it’s how hackers are using them.
We’ve seen thousands of these types of attacks in the last month alone.
Now, we’re seeing another legitimate tool used for these purposes. In this case, it’s Adobe InDesign.
In this attack brief, Check Point Harmony Email researchers will discuss how hackers are using Adobe InDesign to send phishing material.
Attack
In this attack, hackers are creating content in Adobe InDesign to send phishing links.
- Vector: Email
- Type: BEC 3.0
- Techniques: Social Engineering, Credential Harvesting
- Target: Any end-user
Email Example
This email starts as what looks like an invoice. The subject line has both an invoice number and a PO number.
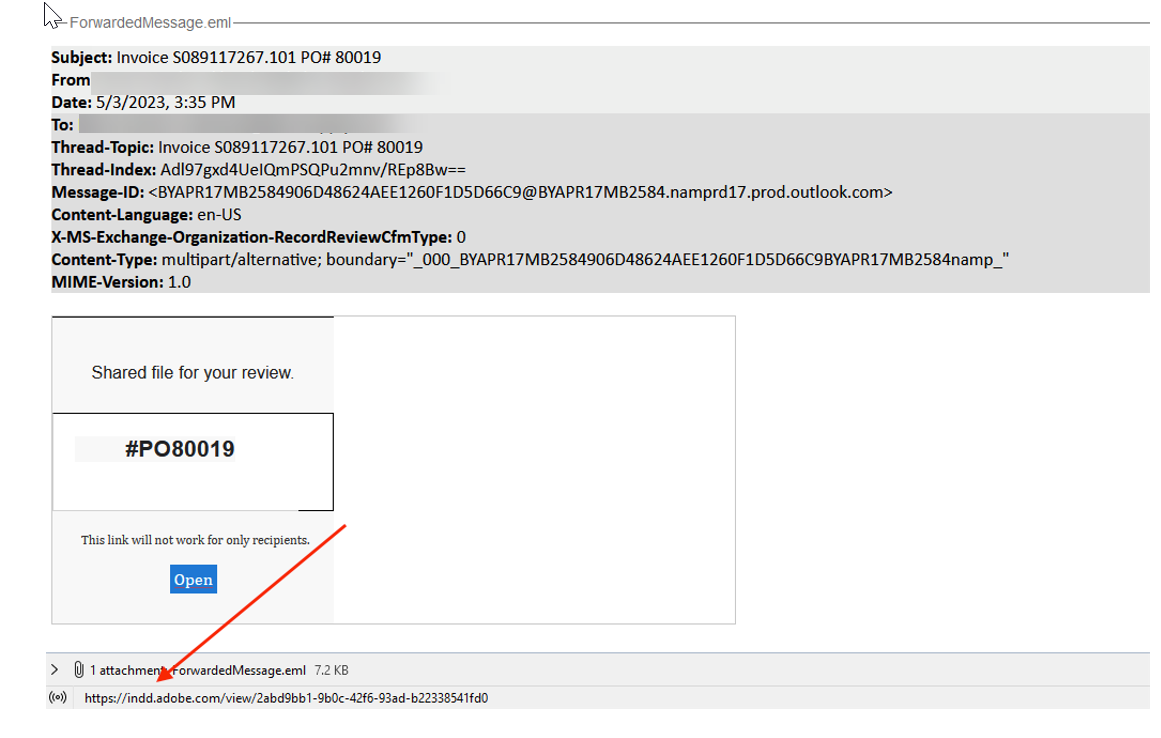
Notice, though, the link. Indd.adobe.com leads to the cloud-based version of Adobe InDesign. On that platform, anyone can create all sorts of documents, from standard invoices to more complex documents. Instead of an invoice or purchase order, it leads to a malicious document.
But because the link itself is legitimate, link scanners won’t think anything of it. And even though it might be odd to receive a statement or invoice via InDesign, Adobe is a legitimate brand. Hovering over the link won’t reveal anything out of the ordinary.
Here's another example. Once again, notice that it comes directly from Adobe (message@adobe.com). It’s a shared PDF file that links to an Adobe page

These attacks make it very difficult for typical cyber hygiene to come into play. Hovering over the URL won’t be as effective. The sender is legit. That makes it very tough for even the most trained user to spot it.
Techniques
BEC 3.0 is about the speed of execution. Instead of spending weeks or months crafting the perfect attack at the perfect time, BEC 3.0 attacks rely on easy-to-use tools that can create legitimate documents that have phishing links or messages embedded within them.
This attack takes advantage of that, by utilizing an easy-to-use, popular tool like Adobe InDesign.
Utilizing these documents to create phishing pages that are sent to the end-user makes the hackers’ job easy. The link is legitimate, so it will go through standard scanners and the end-user.
In this case, you have to emulate behind the link to truly understand what’s going on. That’s not always the case for security services.
Stopping attacks is a bit like playing cat and mouse. A hacker finds something that works. They’re going to keep at it until security services across the board can reliably stop it. Then they will adjust and try something new. And so on. Right now, BEC 3.0 has proven difficult for most security services to stop. And until that happens, hackers will keep at it.
Check Point researchers reached out to Adobe to inform them of this campaign on July 25th.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement full-suite security that can also scan documents and file
- Implement robust URL protection that scans and emulates webpages






