Many countries and cities around the world are instituting a so-called COVID pass. The idea is that an app will show a person’s vaccination status or proof of negative test. This will allow entry into certain places.
One country doing this is England. Through their National Health Service (NHS), the NHS COVID Pass allows for entry to travel abroad, as well as different venues or events around England.
As a critical piece of documentation, hackers are trying to get in on the race. Avanan researchers have noticed hackers spoofing vaccine pass emails. This particular email spoofs England’s COVID pass. Avanan researchers have also seen an uptick in similar emails from France, Portugal, Italy, Switzerland and Spain.
As this requirement extends across Europe and Asia, Avanan researchers expect a continued rise in these spoofed emails.
This email in England, missed by ATP, has been surging, aiming to get valuable credentials, and to rob people of an actual pass. Here’s the email:
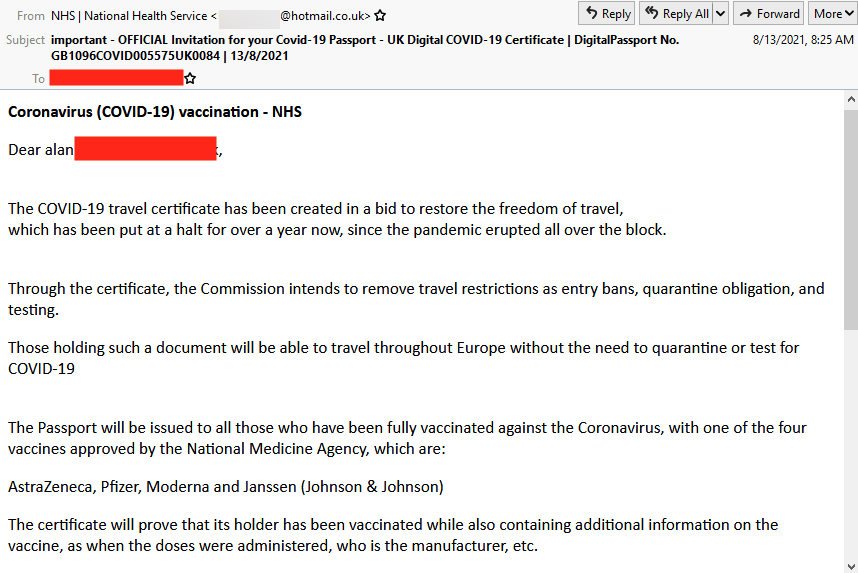
This attack is effective for a number of reasons. There are no links to the site in the email, which allowed it to bypass many traditional phishing filters. The email itself is well-written, with no easily discoverable spelling or grammar errors. (There are some grammar issues if you look closely, but nothing is glaring. The language is also a bit stilted, but not overly so.)
A similar scam took place at the end of June, targeting vacationing Brits. But, as vaccine passports continue in England and in other places, security layers need to adapt.
These hackers will not have to deploy new technologies, but rather tried and true techniques to reach the inbox. They’ll use the Static Expressway, malicious URLs, password harvesters and BEC attacks. This attack highlights how important it is to use a multi-tiered security architecture like Avanan because these attack emails can be caught by Avanan’s AI’s understanding of an organization’s email behavior.







