Check Point researchers have discovered a burgeoning attack taking advantage of public file sharing sites like WeTransfer to host phishing content.
The attack sees phishing links hosted on files on these sites. Though this attack leads to a clear credential harvesting attack, Mimecast marked it as clean. Here's how it breaks down:
Step 1:
It starts by sending a suspected credential harvesting email. In this case, it involves a link to files on WeTransfer, though we've also seen it on SharePoint as well.
The intended target has their email protected by both Mimecast and Avanan/Harmony:
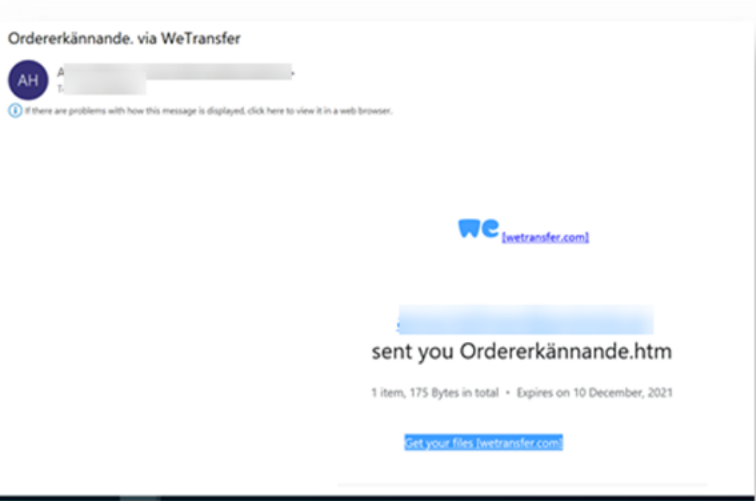
(It's a Swedish word, meaning "Order acknowledgment")
The link is indeed malicious. It goes to a file that contains links to lookalike sites that attempt to harvest credentials. (Think O365 logins).
This is a common trend that we see across many popular sites. In the past, we've written about a similar WeTransfer campaign that also bypassed Mimecast; we've seen hackers host legitimate files on Adobe Cloud, Google Docs, MailGun, Movable Ink and much more.
The reason it works is a broader concept that we call The Static Expressway. All of these sites, including WeTransfer, are on static allow lists. For popular websites, static solutions like Secure Email Gateways automatically trust them, sending content straight through to the inbox. (It would be impossible to block Google, so the alternative is letting anything from Google through.) Hackers know this and upload or host phishing content on legitimate websites.
Step 2: Mimecast miss
Mimecast starts by analyzing the email:
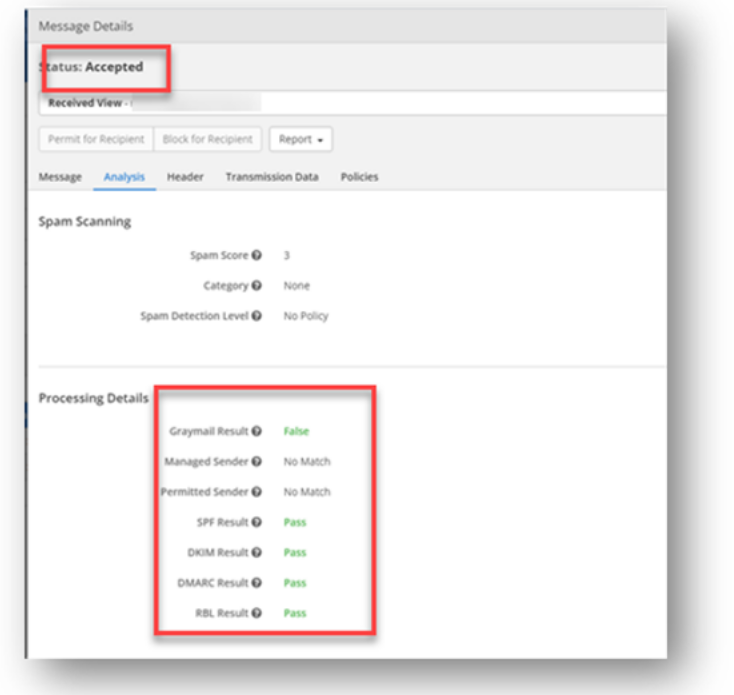
As you can see, Mimecast marks this email as perfectly clean.
Step 3: Avanan/Harmony Block
Avanan/Harmony, working as the last layer before the inbox, catches what Mimecast misses:
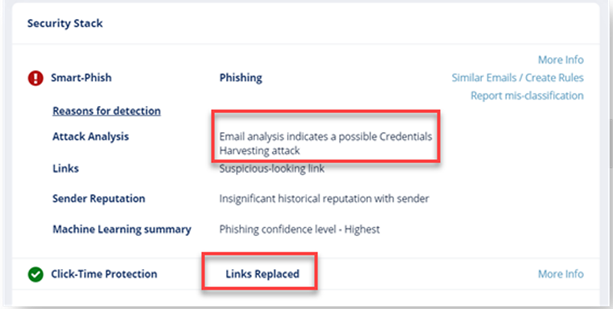
Avanan/Harmony marks this as a credential harvesting attack, noting, in particular, a suspicious link.
Step 4: The Website is Malicious
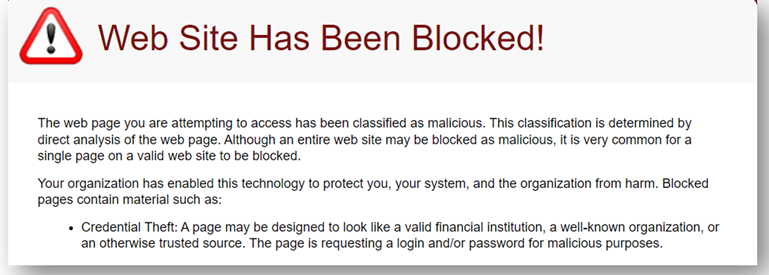
Further analysis shows the malicious nature of the link.







