Business Email Compromise attacks are some of the most pernicious out there. They are an ideal combination of seemingly innocent yet incredibly difficult to stop. The only way to stop them, according to Gartner, is to be deployed inside the cloud email server via API; offer internal email protection between users; use advanced machine learning for internal email context, and offer account take over protection.
External gateways, like Proofpoint, can't do that due to their architecture. Companies like Mimecast and Proofpoint are designed only to monitor inbound email—therefore they have no way of scanning an internal email or understanding the context or conversational relationships within an organization. When an external gateway sees an email from the 'CEO' to the 'CFO', it will be the very first time it has seen such a conversation. While an internal solution will have seen thousands of similar real, internal conversations to compare it to, an external gateway can only guess at the context.
We see this at work in this attack observed by Check Point Researchers. The difference between how Avanan's SmartPhish handles this versus Proofpoint is stark.
Step 1: The Ask
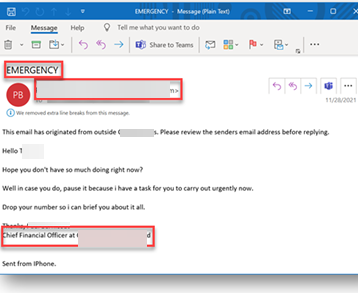
This comes across as an email from the company's CFO. IT has all the classic marks of a BEC attack. They are asking for an urgent task and an immediate reply. The subject line uses classic social engineering tactics. As an end-user, this email could cause you to act. How can you deny an urgent task from someone in the C-Suite?
Step 2: The Miss
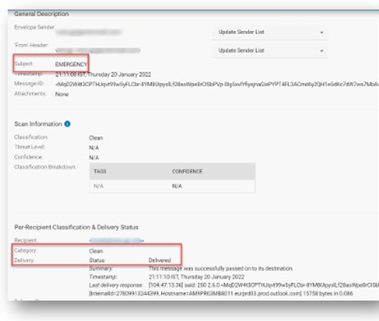
Proofpoint marked this as clean. For gateways like Proofpoint, BEC attacks are incredibly difficult. There's no malware, no malicious URL. Without the internal context, they see this email as a single point in time. It is the first time they have seen such a request from the CFO. They don't know if this is a typical request or not. Because they're blind to the context, they're looking at the wrong things. They are looking for domain or display name spoofing, as well as lookalike domains. Those are not sued in this attack.
Step 3: SmartPhish steps in
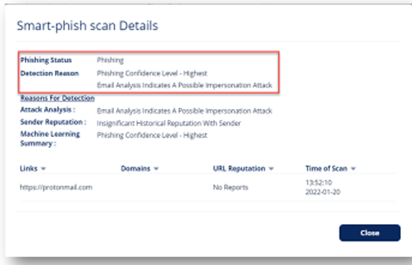
Avanan views this differently. We analyze the signature in the body and understand that the email address does not match. Beyond that, Avanan has all the protections needed to stop BEC. It has machine learning algorithms that combine with role-based contextual analysis of previous conversations to determine the threats that others have missed. On Deployment day, we analyze one year's worth of email conversations to build a trusted reputation network. We scan and quarantine internal email and files in real-time, preventing east-west attacks and insider threats. Finally, we have account takeover protection that goes beyond email, looking at login events, configuration changes and end-user activities throughout the suite.
Step 4: The Investigation Concludes
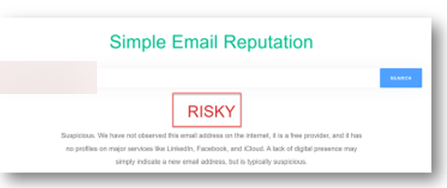
We can see that this email address and email is risky, making this a real threat to anyone who only has Proofpoint.







