When hackers find something that works, they keep going at it until it doesn't.
Think, for example, why so many hackers continually spoof Microsoft at high rates. It's because it works. It gets into the inbox and end-users click on malicious links.
Recently, we've been following how attackers are following this trend with Walgreens.
A few weeks back, we wrote about hackers spoofing Walgreens to get users to give over credentials. Then, we followed it up with another, separate campaign with much the same aims.
Here we are again with another Walgreens spoof. Here's what it looks like:
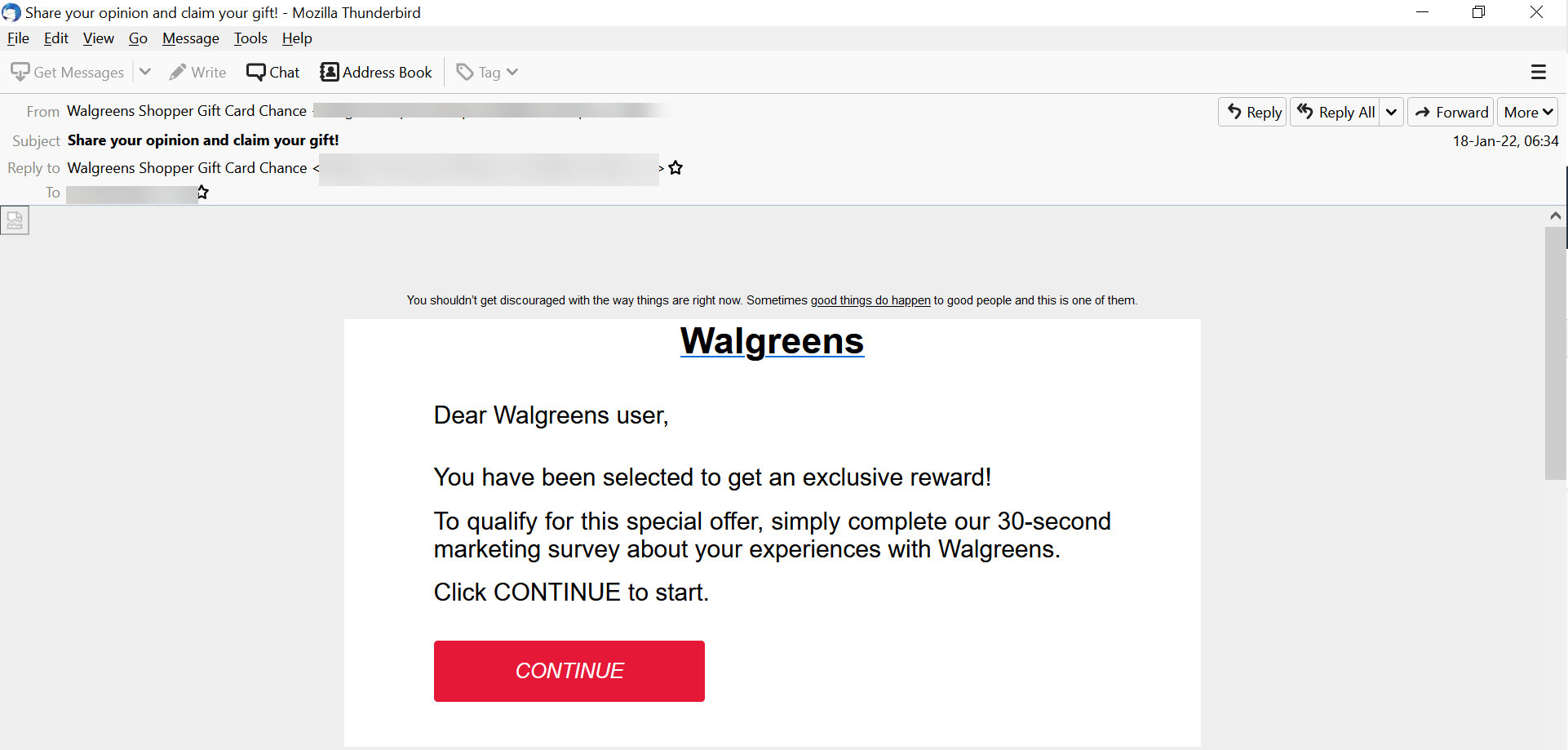
The idea is that, when users provide feedback, they will receive a gift card.
However, the sender address is not from Walgreens. The links don't go to a Walgreens web address. This is a classic credential harvesting email.
And yet, this is another one of many Walgreens spoofed emails that claim some form of reward. That tells us that hackers are finding great success with these sorts of emails.
An additional tactic that these threat actors used was sending this to a listserv. This is an effective technique that we've seen before. It allows the hackers to reach multiple email inboxes with just one message.







