Ransomware and malware remain a primary concern for organizations. In 2023, 1 in every 10 organizations worldwide was hit with an attempted ransomware attack, a 33% increase over 2022.
In 2023, email was once again the favored delivery vector for malicious files. The rise has been stunning. In 2018, just 33% of malicious files were delivered via email. In 2023, that number shot up to 92%.
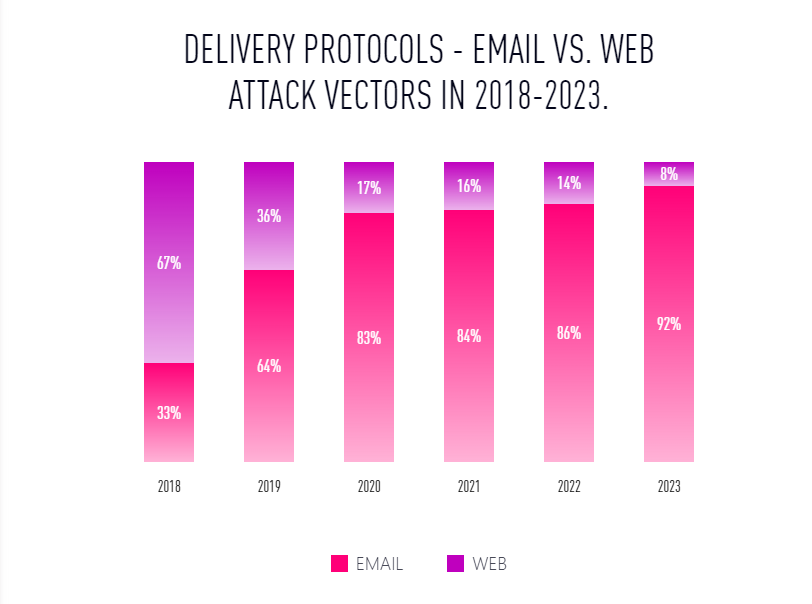
Thus, it’s imperative for organizations to deploy email security with robust malware prevention capabilities.
A new report released by Miercom analyzed the security effectiveness of five different vendors’ next-generation firewalls. Testing was done with a set of zero+1 day (malware no more than one day old) samples that were pulled from publicly available repositories.
When it comes to the prevention of malware, Check Point was by far the most effective, preventing 99.8% of new malware, including executables, documents and archived files that were no more than one day old.
When it came to preventing phishing and malicious URLs, Check Point once again led the way, preventing 100% of the URLs.
How do these tests and statistics relate to email security?
Here’s how:
The Check Point Infinity Platform utilizes the same malware scanning engines. These are AI-powered, ML-driven engines that are purpose-built to prevent malicious documents and files from entering an organization. In all, this is 90 engines—50 of which are AI-powered—that scan over 2.8 billion websites and files a day.
So when Check Point is measured at 99.8% effectiveness for blocking new malware, that applies to Harmony Email & Collaboration customers. If an attacker sends an email with a zero-day malicious file, then Miercom testing found that Check Point will block it 99.8% of the time. If a malicious URL is sent, Miercom found the block rate is 100%.
And, as opposed to many of our competitors, Check Point has a dedicated team of developers and researchers whose sole job is to perfect this sandbox service of Check Point, which is in use across all Check Point products. This provides us with a huge advantage—not only does it keep our sandboxing solution world-class, but it also allows our core email security developers to remain focused on delivering other advanced security and productivity features.
As we mentioned, email remains the primary vector to deliver malicious files, and it has increased in recent years. Another change is the type of files being delivered. Let’s take PDFs, which saw a 15% increase in usage over 2022.
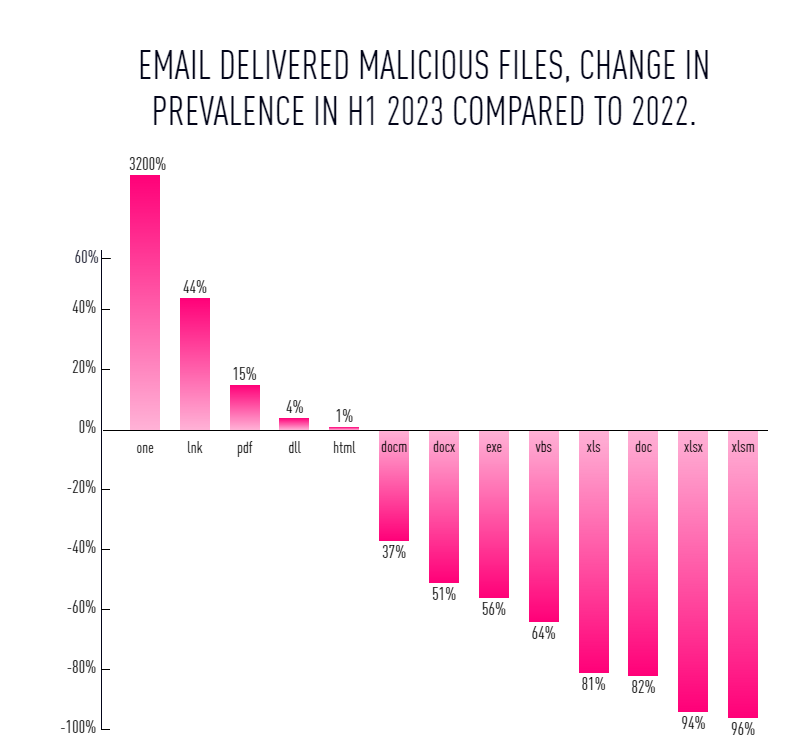
This is particularly relevant due to Qbot, one of the most notorious ransomware groups. Though they were taken down by the FBI last summer, Check Point researchers found a resurgence in Qbot activities starting in December.
And in their campaign, they went back to their bread and butter. The campaign involved sending malicious emails with PDF attachments. These PDFs have embedded URLs linked to a Microsoft installer. This then triggered a new version of Qbot that leveraged an embedded DLL.
This is why malware prevention is so important. It’s even better when you can employ our Deep PDF engine. The engine allows us to examine the PDF structure, embedded images, URLs and raw content. We can then search for characteristics such as URL placement on the document and image placement.
The two main tenants of our malware protection are threat emulation and threat extraction.
With Threat Emulation, we quickly inspect files and run them in a virtual sandbox to discover malicious behavior. Discovered malware is prevented from entering the network. The ThreatCloud Emulation service reports to the ThreatCloud and automatically shares the newly identified threat information with other Check Point customers. The Threat Emulation engine picks up malware at the exploit phase, before it enters the network.
With Threat extraction, we can remove exploitable content, including active content and embedded objects, reconstruct files to eliminate potential threats, and promptly deliver sanitized content to users to maintain business flow.
And then there’s URL protection. As Miercom said, “Check Point demonstrated not only static ability, but could also detect phishing websites dynamically with AI-based phishing protection, based on analysis of web page content such as corporate logos/icons, suspicious fields, irregular spellings, redirection and many other obscured maleficent components of these websites. This double layer of protection is important as many phishing websites change their IP address locations and domain names to defeat static reputation-based forms of protection.”
Beyond this, we have the ability to re-write links inside attachments, giving us a third layer of protection for cases where the attacker weaponized the content behind the link only after the email was sent and inspected.
An email security solution needs to be complete. And with the most accurate phishing engine and the most accurate malware prevention engine on the market, it’s hard to get more complete than Harmony Email & Collaboration.






