Many email security vendors are now heavily relying on sender domain reputation as an indicator of phishing. Avanan's research has found that 43.35% of all phishing attacks are from low-trust domains. To adapt, attacks are utilizing services that lend them credibility. Recently, we wrote about the PhishGun attack, where attackers use services like Mailgun for their attacks; today, we've uncovered an attack whereby hackers are leveraging a service called Flexitive to launch their scams.
Flexitive is an HTML5 design tool that allows you to build content and share it easily. This is a very appealing tool for attackers because they can now design a simple HTML page with malicious links embedded in it; because Flexitive is a legitimate service with a lot of traffic, most email security vendors will allow links from Flexitive. Flexitive also offers a free preview of the custom webpage that the attacker designed, accessible by a link. Avanan has seen 892 Flexitive phishing links in the last week out of 986 total Flexitive links.
For traditional static security solutions to find these attacks, they would have to scan the content inside a Flexitive page to determine whether the Flexitive link is malicious.
Avanan finds these attacks by training our AI to learn the language and style of a phishing email and then uses static levels like sender reputation to convincingly determine that these are phishing emails.
Avanan’s AI was able to determine the email shown below was phishing because of the suspicious text used in the subject and body of the email.
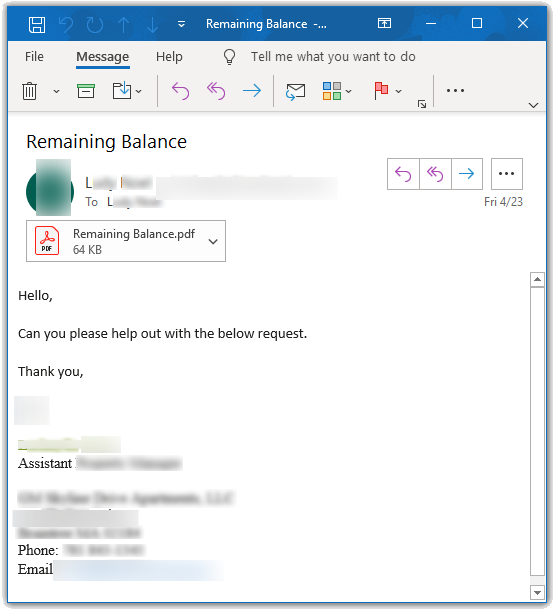
Static layers such as sender reputation would actually not be helpful in this particular case because the attackers sent this targeted phishing attack from a vendor that the victim often communicates with. Avanan’s AI determined that, based on the sender's relationship, it is not normal for this regular correspondent to send attachments with links.
Once the PDF attachment is opened, we can see a Microsoft Office 365 impersonation attempt with a link to a Flexitive webpage.
The webpage has since been taken down by Flexitive or the free page preview has simply expired, but this is what it looked like:
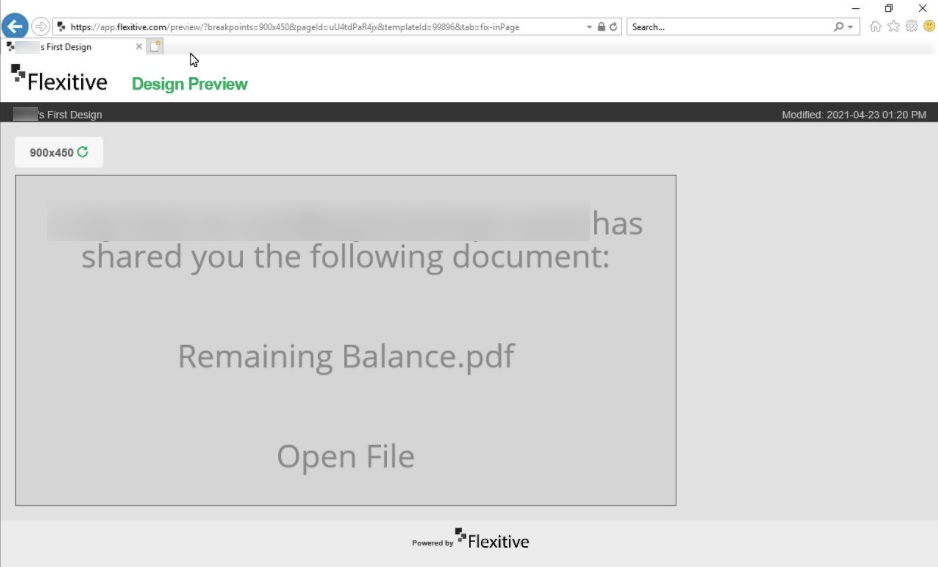
Once the victim clicks on the “Open File” button on the Flexitive page, they will be taken to the malicious website, which is a spoofed Microsoft login page.
These sophisticated and layered attacks are very expensive to detect with traditional security solutions and therefore are slipping past ATP and Legacy gateways. However, with the implementation of a sophisticated AI that knows what a phishing email looks like, Avanan is able to stop these threats in their tracks.







