A new report has found that the construction industry is most at risk for ransomware attacks.
The report, from NordLocker, analyzed 1,200 ransomware cases since 2020 and found that the construction industry had been hit 93 times, the most of any other industry.
Starting in September 2021, Avanan observed a new crypto extortion attack aimed at the construction industry. The attack aims to extract bitcoin by threatening to release incriminating and embarrassing information. In this attack brief, Avanan will analyze the company’s most recent discovery of this crypto-based extortion attack.
Attack
In this attack, hackers are utilizing domain impersonation to get into the inbox and extortion to extract money from the end-user.
- Type: Extortion
- Techniques: Domain Impersonation, Extortion
- Target: Any end-user
In this attack, hackers perform domain impersonation to get into the inbox, followed by an extortion message in the body of the email to induce users to pay.
Email Example #1
In this email, hackers try to get the user’s attention with a subject line that says, “You have an outstanding payment.”
However, in the body, there is a classic extortion email. The sender purports to have installed a Trojan virus that captures all of the end-users clicks. Beyond that, the sender has gathered information that would be used for sexual blackmail.
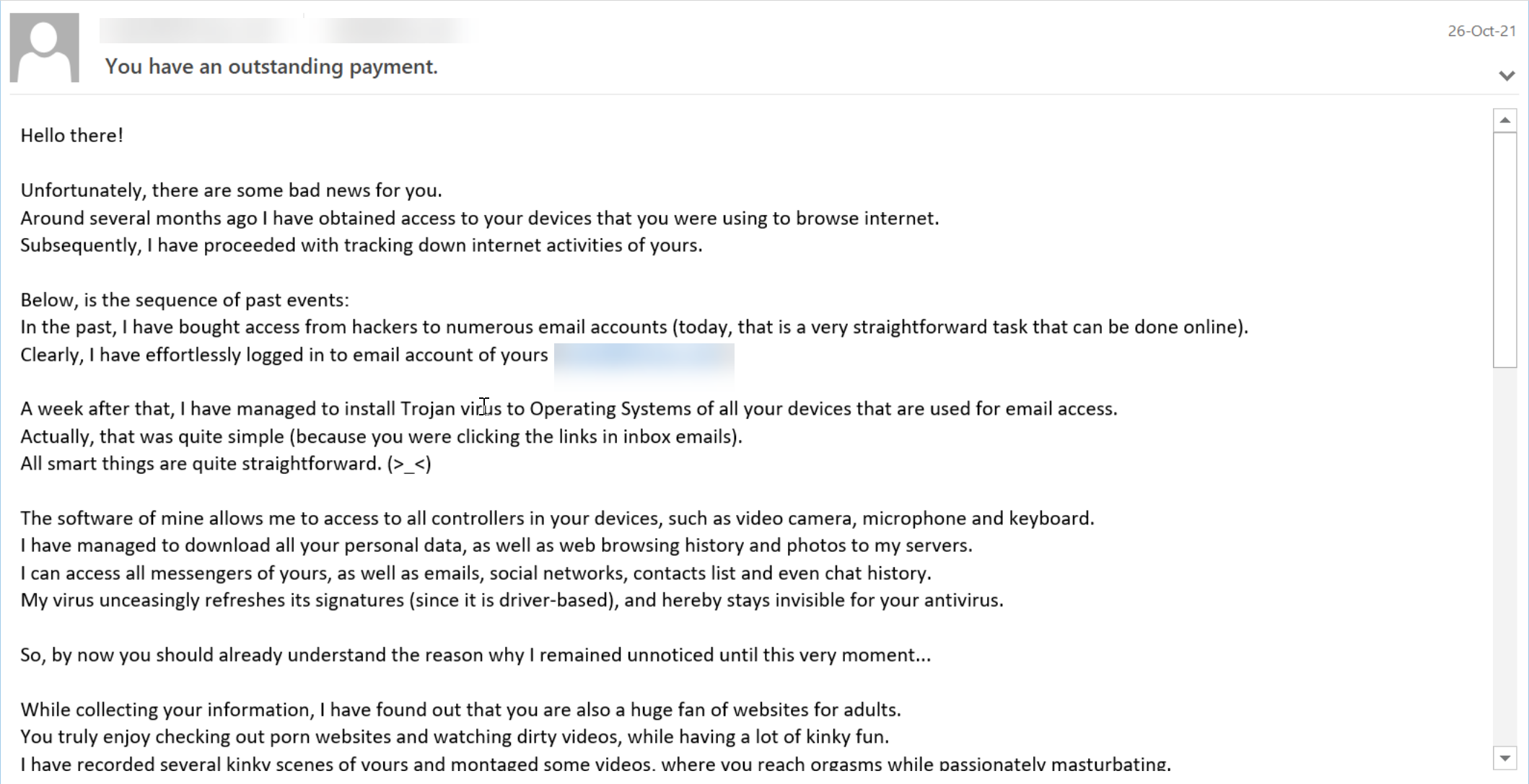
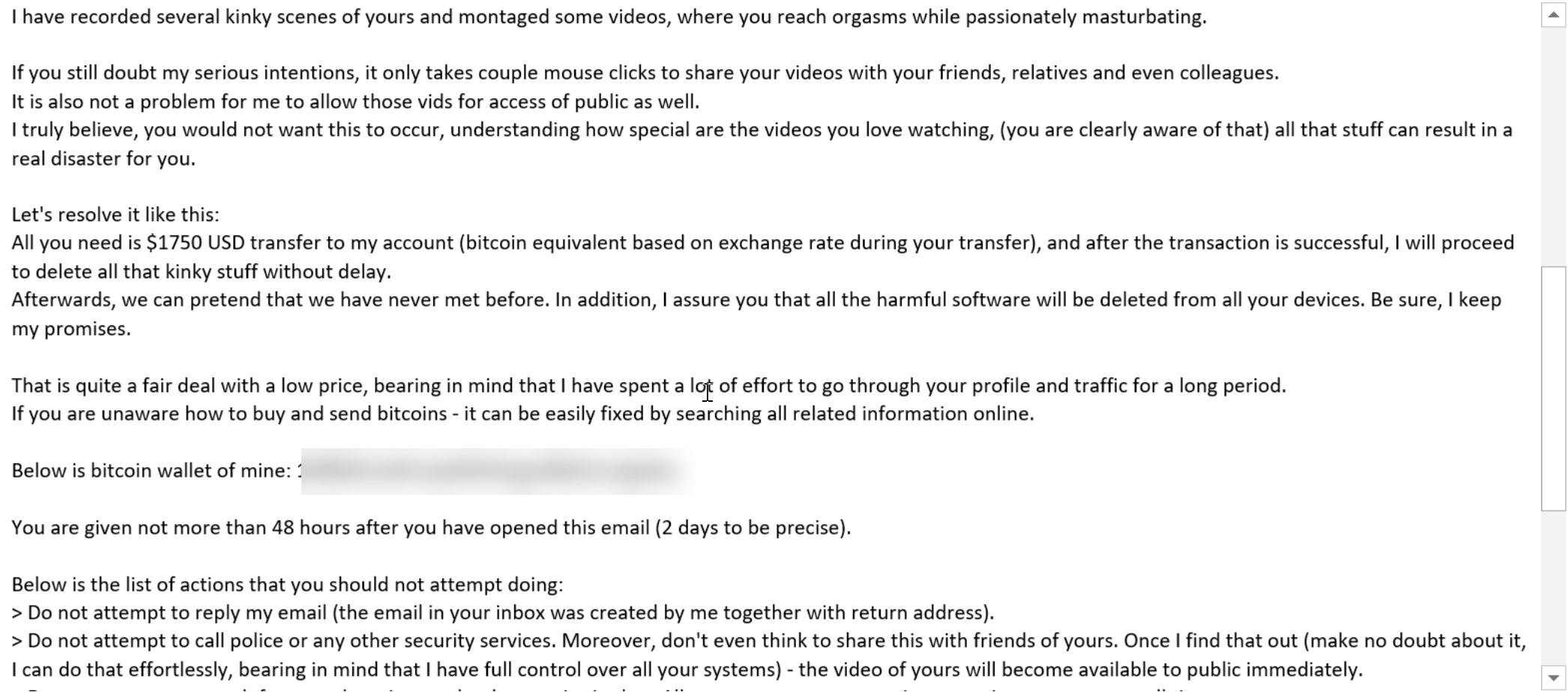
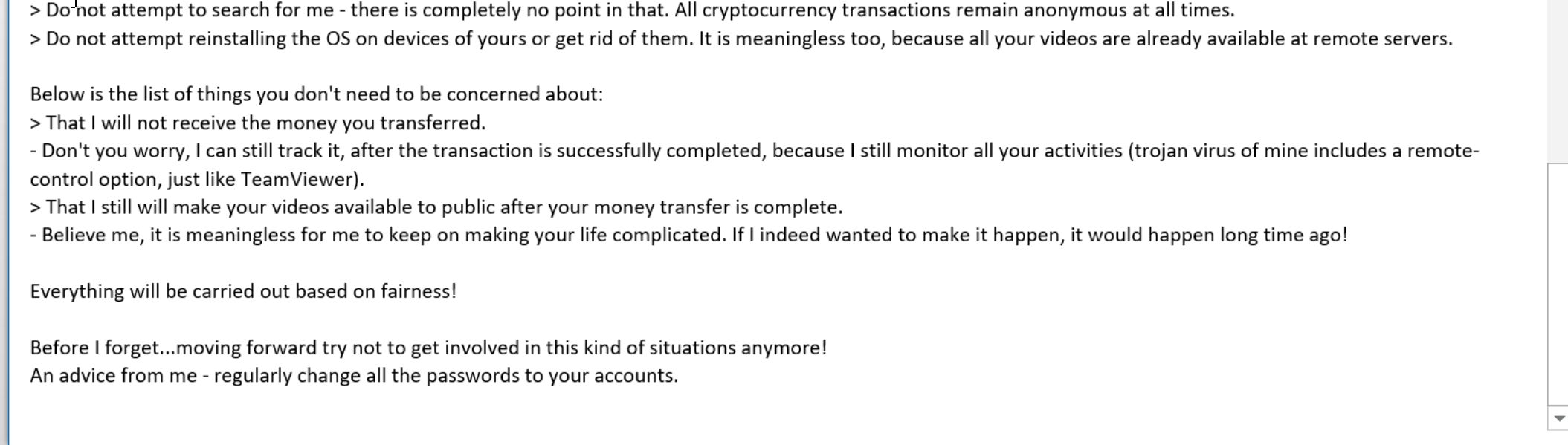
This email claims that, unless money is paid, embarrassing videos will be released.
Techniques
This email is a classic extortion campaign.
According to Check Point Research, these sorts of emails are increasing in regularity:
Number of total related emails:
Number of unique clients
Number of unique recipients
This email asks for the user to pay via a crypto wallet. One of Avanan’s unique indicators of a potential phishing attack is the presence of a bitcoin wallet. As we found in our Global Phishing report, 98% of emails containing a crypto wallet address are phishing.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Encourage end users to immediately alert IT of any email containing extortion-like language
- Implement a security architecture that uses the existence of a crypto wallet as an indicator of attack
- Remind end-users to not click on bitcoin wallets and certainly not pay