There are few things better than receiving a bonus at work for a job well done.
There are also few things worse than being on the receiving end of a bonus email—that's fake. Ouch. Not only are you not getting some extra dough, you're also giving up your credentials.
Talk about the true definition of a bad day at the office.
The Attack: Avanan researchers discovered a new phishing email that looks like this:
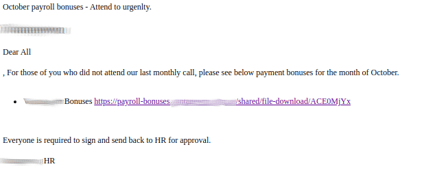
Though there are a few clear cut errors—"urgenlty" is spelled wrong, other grammar mistakes abound—if you were to click on the link, you'd be directed to this page:
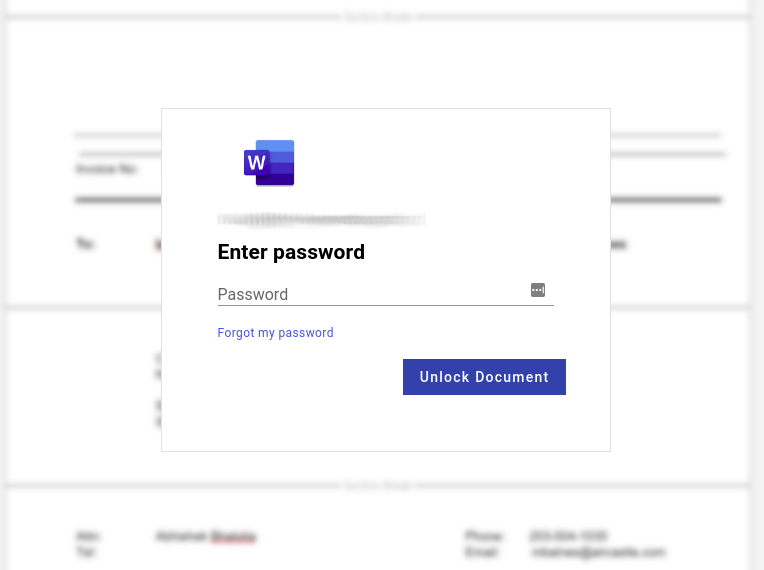
Instead of entering your password to receive a bonus, you're giving it directly to attackers.
Though Avanan stopped this attack, it passed by Proofpoint scanners.
How? Check out the source code behind the email:
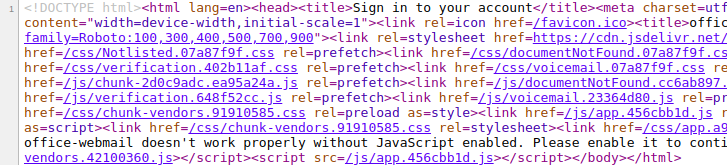
Hackers were smart here. This source code only works by redirecting to domains that are already known to bypass Proofpoint.
Why it Matters: Beyond the inherent frustration from a bonus scam—see the outpouring of anger from Tribune employees, who got a bonus notification as a phishing training exercise—this attack is particularly shrewd because it leverages Proofpoint against itself. By using redirects that already pass Proofpoint, it's a slam dunk for the hackers.
Avanan stopped this attack, because one of our detection layers uses the hacker's own techniques to help identify the attack.Our algorithm looks for known obfuscation methods as Indicators of Attack, so by using these methods they self-incriminate themselves simply by using it.







