We have been tracking the next wave of Business Email Compromise attacks. It relies on the use of legitimate services to unleash attacks. There’s nothing fake or spoofed about these emails. These are legitimate emails, sent from legitimate sites, that link to or include malicious instructions.
This means that hackers take the services that we use every day, and weaponize them against users. And this is done without anything inherently malicious in the email. Plus, it’s trusted by security services and users.
In short, it uses legitimate sites for illegitimate purposes.
In this Attack Brief, researchers at Avanan, a Check Point Software company, will discuss how hackers are creating malicious landing pages in Squarespace, a website building and hosting company, which bypass VirusTotal.
Avanan researchers reached out to Squarespace on May 8th via their report phishing feature to inform them of this attack and research.
Attack
In this attack, hackers are creating free Squarespace accounts and leveraging their domain legitimacy to create pages that have phishing embedded within them.
- Vector: Email
- Type: BEC 3.0
- Techniques: BEC, Social Engineering
- Target: Any end-user
Email Example #1
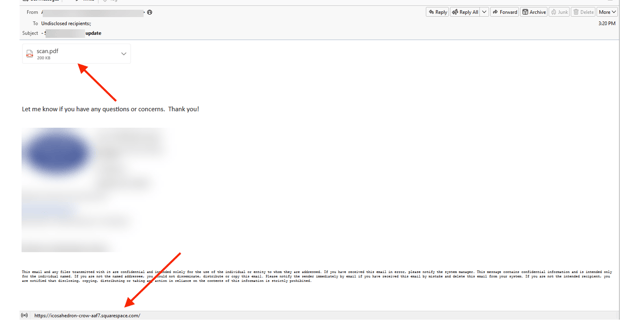
This email starts innocently enough. It’s an email containing a PDF attachment that is actually a link to a URL. The email doesn’t actually come from Squarespace. It’s a regular email from one person to another. When you click on the PDF, however, you are redirected to a page hosted on Squarespace. That is the hackers’ trick. What they are betting on is that the email security service will scan the link and see that it goes to Squarespace. Because Squarespace is clean, the link that’s hosted on Squarespace goes unnoticed. It’s interesting that it’s sent to undisclosed recipients, as that can be a trick for hackers to send one email to multiple people. However, in reading this email, users would have no reason to think something is off.

Users are redirected to this site. It is hosted on Squarespace. Hackers can easily create a free account. Any free domain goes with the following format: username.squarespace.com. This URL follows that same path. Since Squarespace is a legitimate site, this particular domain passes VirusTotal checks.
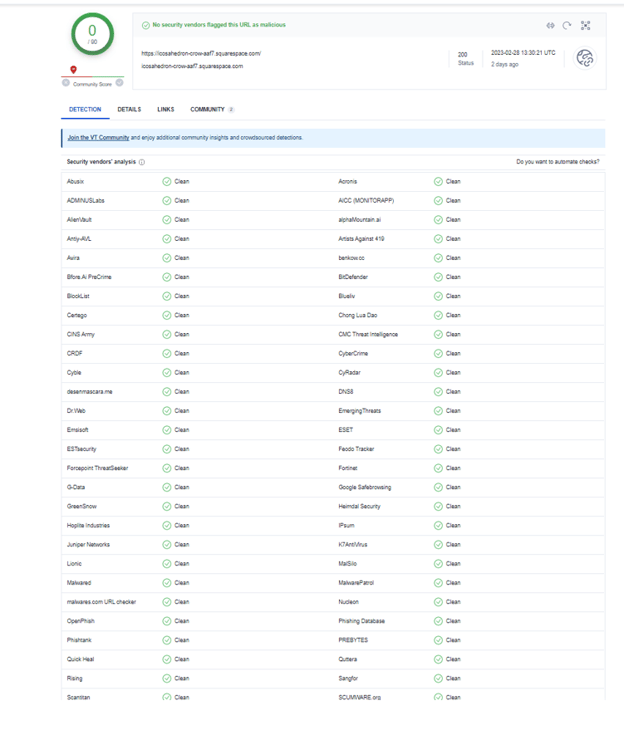
That’s because the URL itself is legitimate. It’s the content on the website that’s problematic. You’ll see the hackers mocked up a page that looks like OneDrive. When clicking on the link, that’s when users are given a malicious download instead. Users have to specifically click on the “OneDrive” link for the download to occur.
Techniques
BEC attacks are everywhere. Most people are seeing a compromised partner or employee inserting themselves into an email thread and changing bank routing details. These are difficult attacks for security services to stop and users to spot. However, using things like NLP, AI and ML makes it possible to stop.
BEC 3.0 represents an entirely different challenge. Everything in the email is legitimate. It comes from a legitimate domain. The text won’t set off alarm bells. The URL is legitimate. In short, the email itself is clean.
But the actions taken after the email are malicious. You have to look past the content and even the context of the email as you do in BEC 2.0, and you have to emulate the webpage and emulate the user actions. You have to look at everything–not just the email.
That is where browser security becomes so important. Good browser security is a great complement to good email security. Why? Because users should be protected everywhere they go, especially when clever attacks like this one nest the malicious payload a few layers past email. Good browser security principles include inspecting sites directly within the browser, analyzing the visuals, text, domain and more for phishing indicators, both known and unknown. Beyond that, emulating every downloaded file in a sandbox for malware is critical, especially since many of these links lead directly to downloads.
These attacks are on the rise, with thousands of BEC 3.0 variations being aimed at end-users in recent weeks.
Cybersecurity is the ultimate cat-and-mouse game. Hackers find an attack technique that works. Security services respond and figure out a way to stop it. Hackers find a new method. And so on.
Right now, hackers are about to hit BEC 3.0 at full steam.
Is your security system ready?
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that looks at all URLs and emulates the page behind it
- Educate users on this new variant of BEC






