Recently, Check Point Research (CPR) made an alarming discovery in Latin America - an ongoing campaign deploying a fresh variant of the BBTok banking malware. This new variant has replicated the interfaces of more than 40 Mexican and Brazilian banks, fooling unsuspecting victims into divulging their 2FA codes or payment card numbers.
Originally unveiled in 2020, the BBTok banking malware has made its mark in Latin America through its insidious file-less attacks. This malicious software boasts a wide range of capabilities, including the ability to enumerate and terminate processes, manipulate keyboard and mouse functions, and even tamper with clipboard contents. Not stopping there, BBTok also encompasses classic banking Trojan features, luring unsuspecting victims into fraudulent login pages that imitate numerous banks across Mexico and Brazil.
Since it was first publicly disclosed, the BBTok operators have adopted new TTPs, all while still primarily utilizing phishing emails with attachments for the initial infection. Recently we’ve seen indications of the banker distributed through phishing links, and not as attachments to the email itself.
To effectively manage their campaign, the BBTok operators created a unique flow kicked off by the victim clicking a malicious link, likely sent in a phishing email. When a victim clicks the link, it results in the download of either a ZIP archive or an ISO image, depending on the victim’s operating system. Although the process is seamless for the victim, the server generates a unique payload based on parameters found within the request.
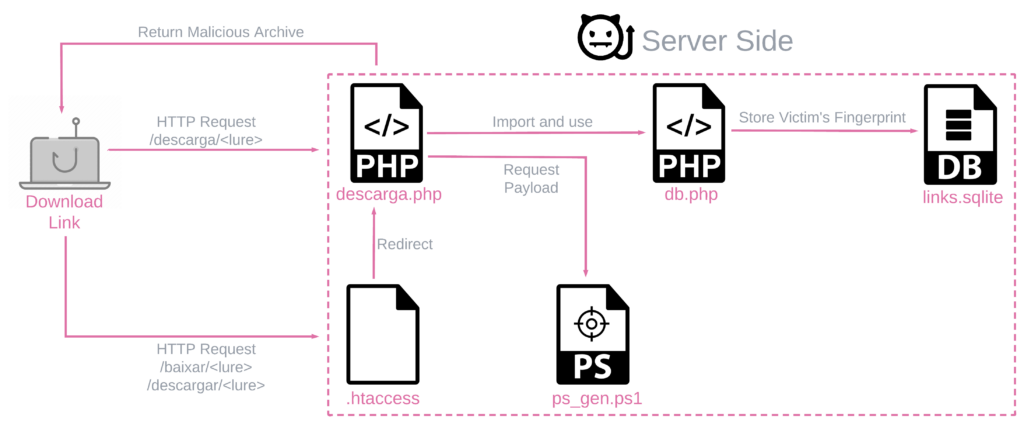
Upon accessing the malicious link, an ISO or ZIP file is downloaded to the victim’s machines. Those contain an LNK file that kicks off the infection chain, leading to the deployment of the banker while opening a decoy document. Although the process appears to be quite straightforward upon first glimpse, we’ve found evidence that there’s a lot going on behind the scenes.
The BBTok banking malware has a dedicated functionality that replicates the interfaces of more than 40 Mexican and Brazilian banks, and tricks the malware victims into entering their 2FA code to their bank accounts or into entering their payment card number. An analysis of the payload server-side code revealed the actors are actively maintaining diversified infection chains for different versions of Windows.
Posing as legitimate institutions, these fake interfaces coax unsuspecting users into divulging personal and financial details, tricking the victim into entering the security code/ token number that serves as 2FA for bank accounts and to conduct account takeovers of the victim’s bank account. In some cases, this capability also tricks the victim into entering their payment card number.

Figure 1 – Examples of fake interfaces embedded within the BBTok Banker
During the research, CPR were able to identify a database of some BBTok malware victims in Mexico, that contained over 150 entries with victims’ information:
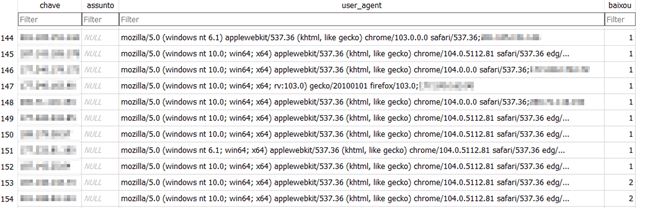
Figure 2 – Database with victims information
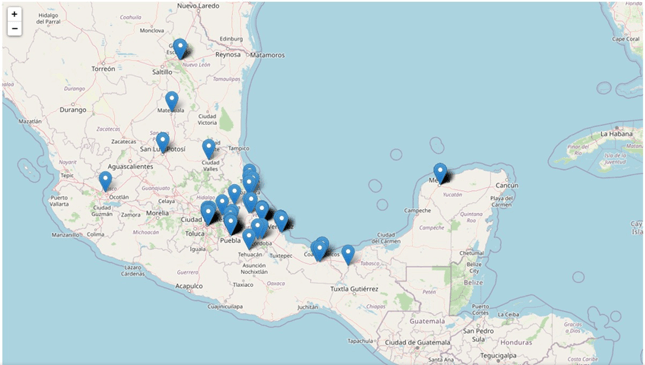
Figure 3 – Geographical distribution of the victims within Mexico
Summary
Despite its ability to evade detection with its elusive techniques and focus on targeting victims exclusively in Mexico and Brazil, it is clear that BBTok continues to be actively deployed. With its multitude of capabilities and its innovative delivery method involving LNK files, SMB, and MSBuild, this banking malware still poses a significant threat to both organizations and individuals in the region.
Gaining a close look at the attackers' workbench is a rare occurrence for security researchers, and even rarer is the chance to witness its evolution over time. Our recent findings have only strengthened our belief that all threat actors, including those driven by financial motives, are constantly adapting and enhancing their methods. They diligently keep up with new security trends, exploring fresh ideas and seizing new opportunities. In order to effectively safeguard against future attacks, security researchers must do the same.






