Avanan analysts have recently discovered an exploit vector in Google Docs that attackers are using to deliver malicious phishing websites to victims.
Here is what an attack email can look like:
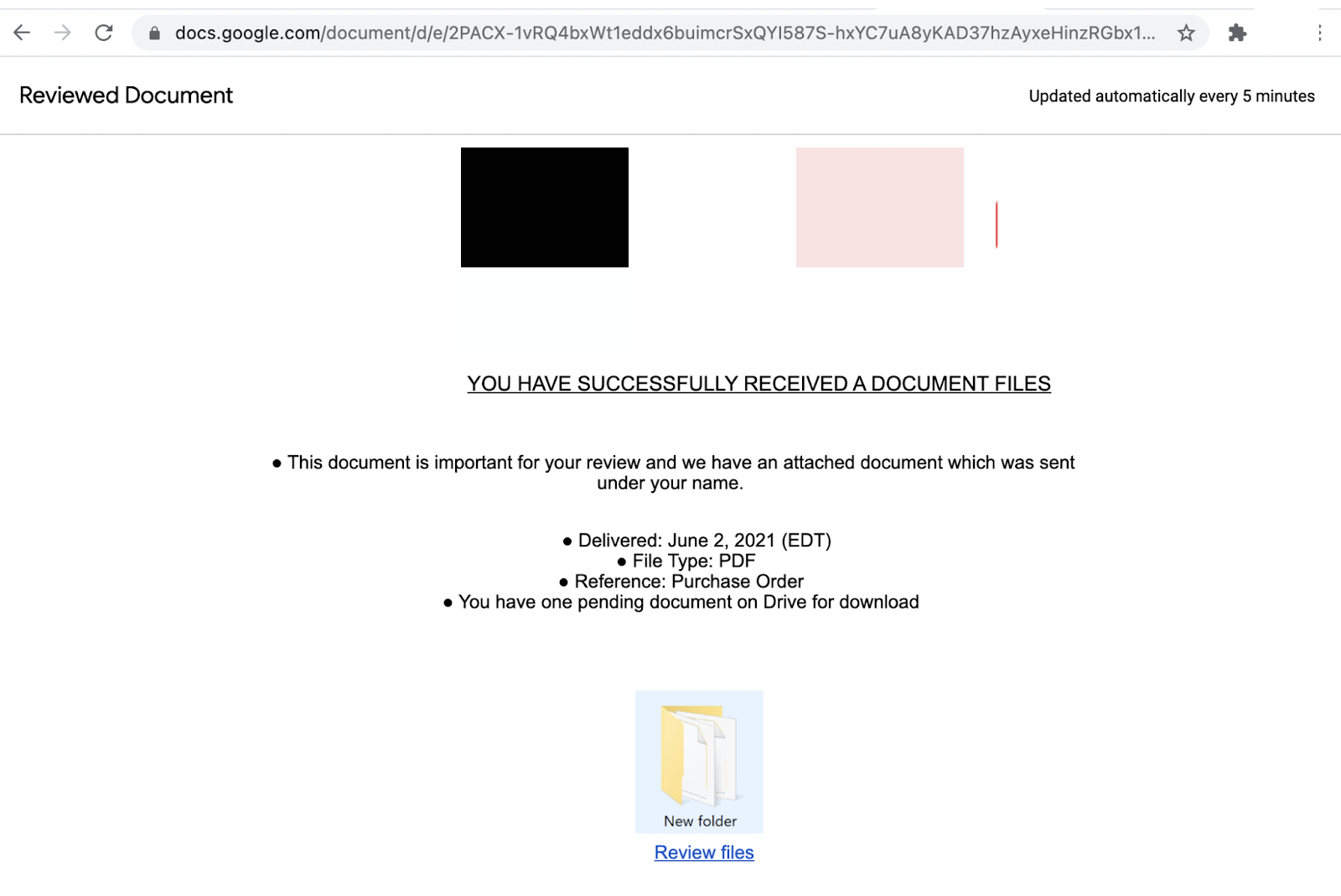
That link leads to this Google Docs page:
.png?width=1492&name=pasted%20image%200%20(18).png)
This Google Docs page may look familiar to those who share Google Docs outside of their organization. This, however, isn’t that page. It’s a custom HTML page made to look like that familiar Google Docs share page.
The attacker wants the victim to “Click here to download the document” and once the victim clicks on that link, they will be redirected to the actual malicious phishing website where their credentials will be stolen through another webpage made to look like the Google Login portal. As you can see, that is not Google’s website.
How does the attacker accomplish this?
This attack is actually quite simple to execute mainly because Google does most of the work for the attackers.
Step 1. Write a webpage that resembles a Google Docs sharing page:
Step 2. Upload that HTML file to Google Drive:
Google will be very helpful and once the file is scanned, they will automatically render the HTML.
You can see the page preview here:
Step 3. Right-click the uploaded file and open it in Google Docs:
This is the clever bit because if you simply click “Get link” you would only see the source code of the file, not the rendered version.
Here’s what the page looks like in Google Docs:
Here's what the page would have looked like if the attacker selected “Get link”
Clearly, the attacker wants the top version, with the rendered image.
Step 4. Publish to the Web:
To make the file render properly to the victim, the attacker has to select “Publish to the Web” from the “File” dropdown menu.
Then, the attacker will have to click “Embed” and “Publish”:
Once published, Google will provide a link with embed tags that are meant to be used on forums to render custom content. The attacker does not need the iframe tags and only needs to copy the part with the Google Docs link as shown below:
This link will now render the full HTML file as intended by the attacker and it will also contain the redirect hyperlink to the actual malicious website.
.png?width=1492&name=pasted%20image%200%20(19).png)
Step 5. Simply insert this link into an email and hit Send!
Other Examples
Avanan analysts also spotted this same attack method used to spoof a DocuSign phishing email.
In this case, the “View Document” button was a published Google Docs link that in fact was a fake DocuSign login page.
.png?width=1384&name=pasted%20image%200%20(16).png)
This phishing page had an embedded listener on the “Log In” button which would transmit the entered password to an attacker-controlled server:
Conclusion
Hackers are bypassing static link scanners by hosting their attacks in publicly known services. We have seen this in the past with small services like MailGun, FlipSnack, and Movable Ink but this is the first time we’re seeing it through a major service like Google Drive/Docs.
This attack highlights how important it is to use a multi-tiered security architecture like Avanan because these attack emails can be caught by Avanan’s AI’s understanding of an organization’s email behavior.






