Prevent account takeover with Avanan. Identify past breaches and remediate easily.
Pattern Analysis for Compromised Accounts
Avanan’s event analysis algorithm identifies behavior that can be a sign of account takeover events.
Prevent account takeover with Avanan. Identify past breaches and remediate easily.
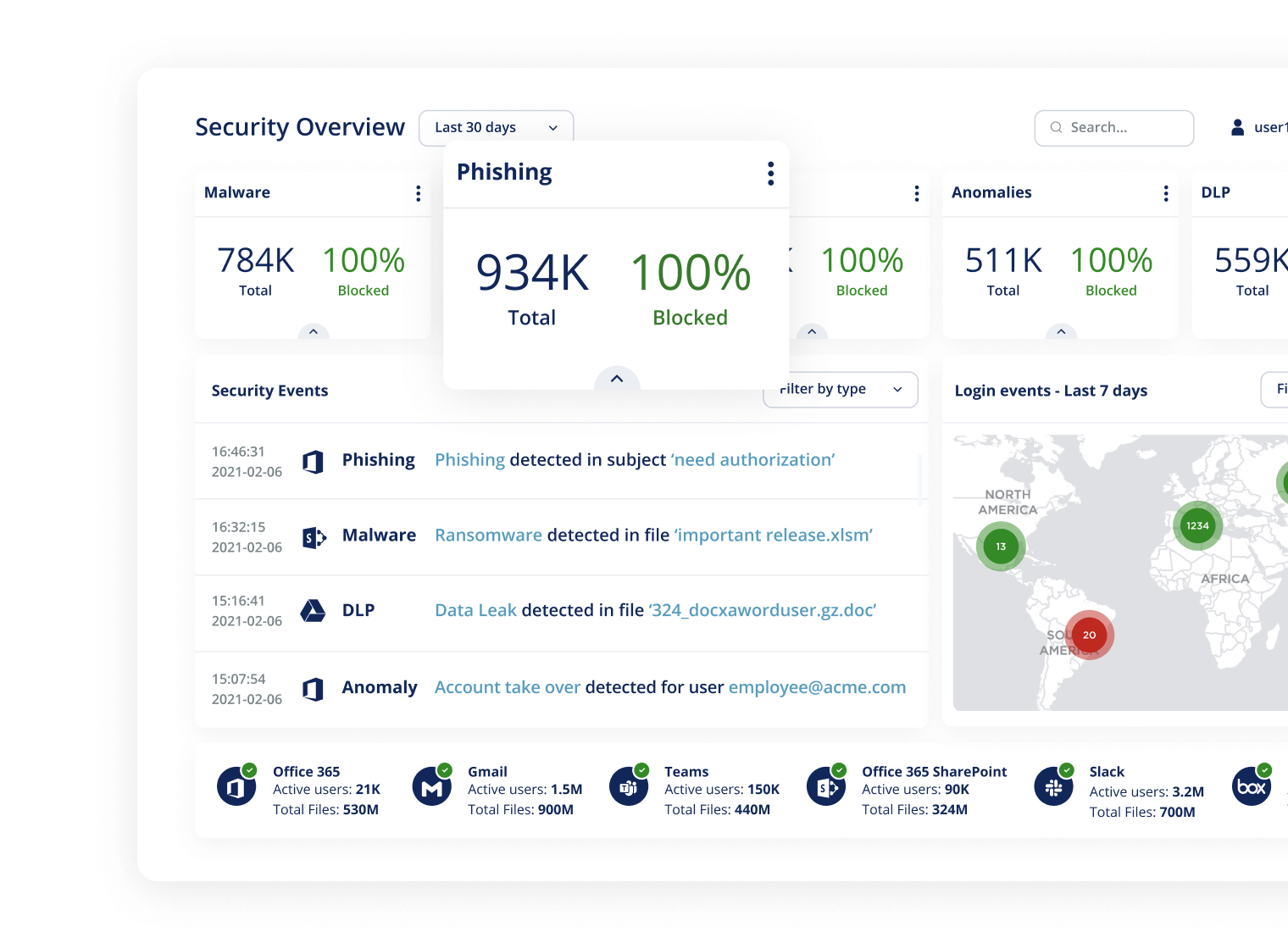
Avanan’s event analysis algorithm identifies behavior that can be a sign of account takeover events.
When we connect to a customer's cloud app, we capture year’s worth of historical information to create a model of each user, as well as an organization’s custom threat profile. Within each SaaS, we monitor over 100 event indicators and correlate them to identify compromised accounts.
These indicators are fed into ML algorithms that’s trained to find attacks and filter out false positives. This applies to past accounts breached before installing Avanan, and works to prevent new takeovers.
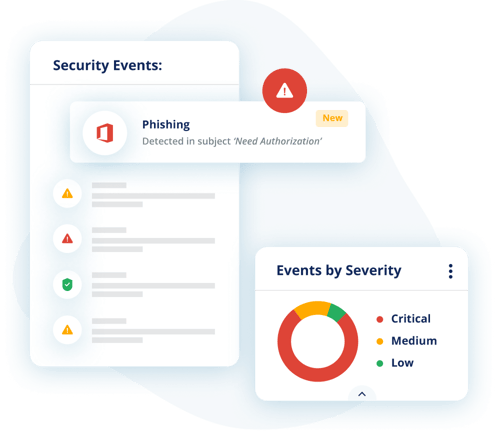
Logins from new devices, locations, or browsers
Suspicious mailbox configurations
Insecure or malicious mail configurations
Disabling of multi-factor authentication
Suspicious internal emails with multiple recipients
Multiple password resets in short period of time
Changes in contact groupings
Changes in session characteristics
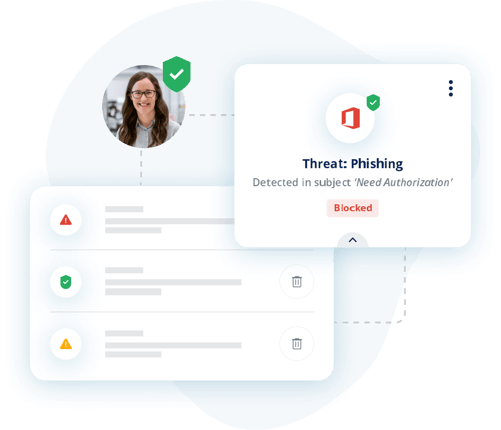
Avanan has a unique combination of account takeover abilities. From real-time prevention, historical breach detection, and adaptive false positive filtering, Avanan provides the most advanced protection of account takeover.
Caught a tremendous amount of threats that ATP and Zix SecureGateway left unchecked. Avanan has been our most reliable email security layer in our organization.
Visualization Engineer, Finance Industry
We selected Avanan over Email Laundry, Mimecast and Proofpoint. Their design is much more cutting edge and simpler to implement.
CTO, Retail Industry
Avanan has proven to be a better option than Microsoft ATP. Start directly with Avanan instead of ATP
Infrastructure and Operations, Communications Industry
We were receiving too many phishing emails. Avanan is stopping all of them.
Systems Integrator, Manufacturing Industry
The solution was extremely simple to implement and integrated into our current service offerings. We spent less than one day with the onboarding team and began to see results immediately.
Senior IT Administrator, Manufacturing Industry
Do a trial. It's easy to set-up and they will be able to immediately show you how they can improve your email security.
Manager of IT, Construction Industry