Avanan uses advanced AI to prevent malicious
attacks from ever reaching your inbox.
The Avanan Difference
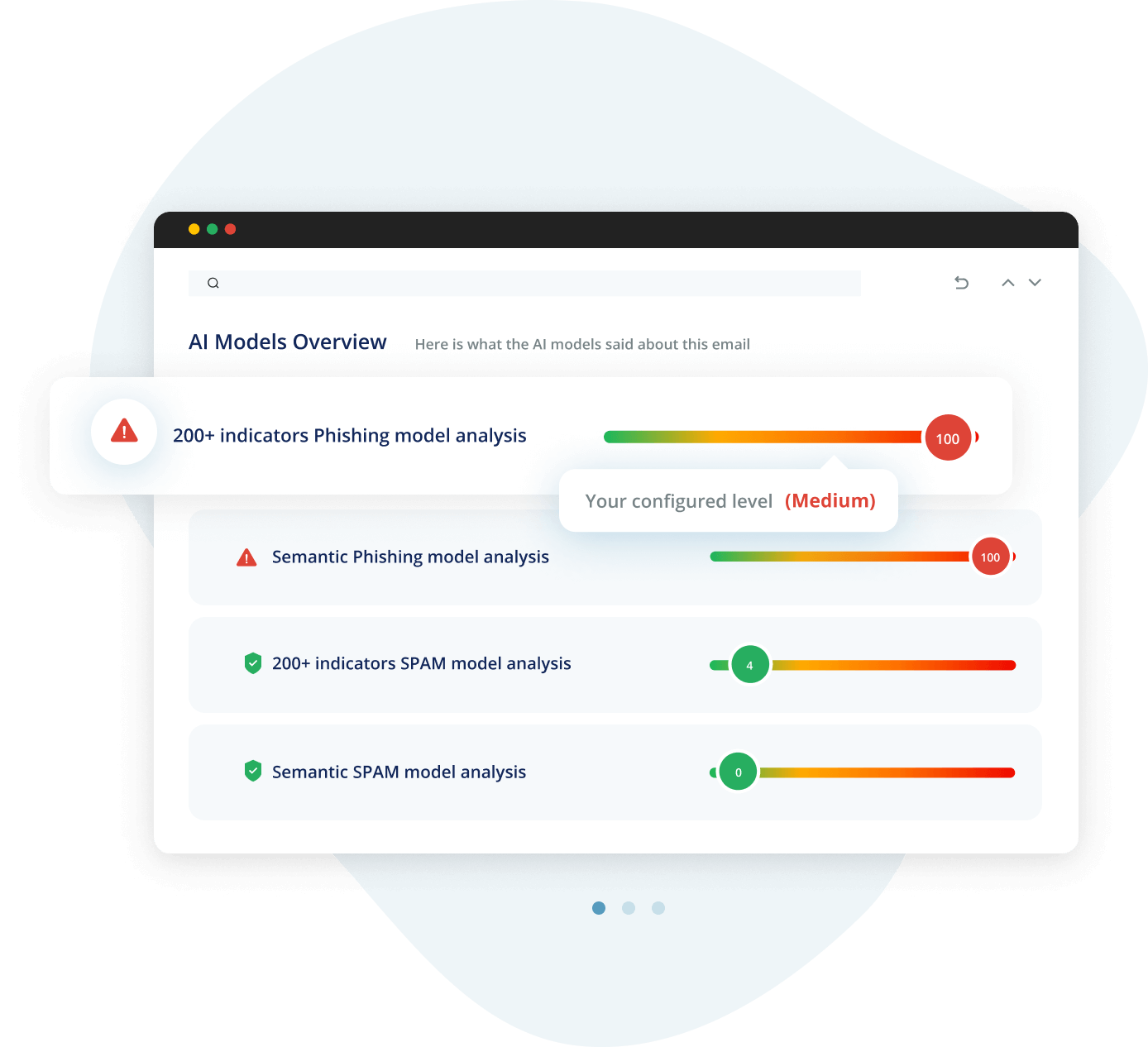
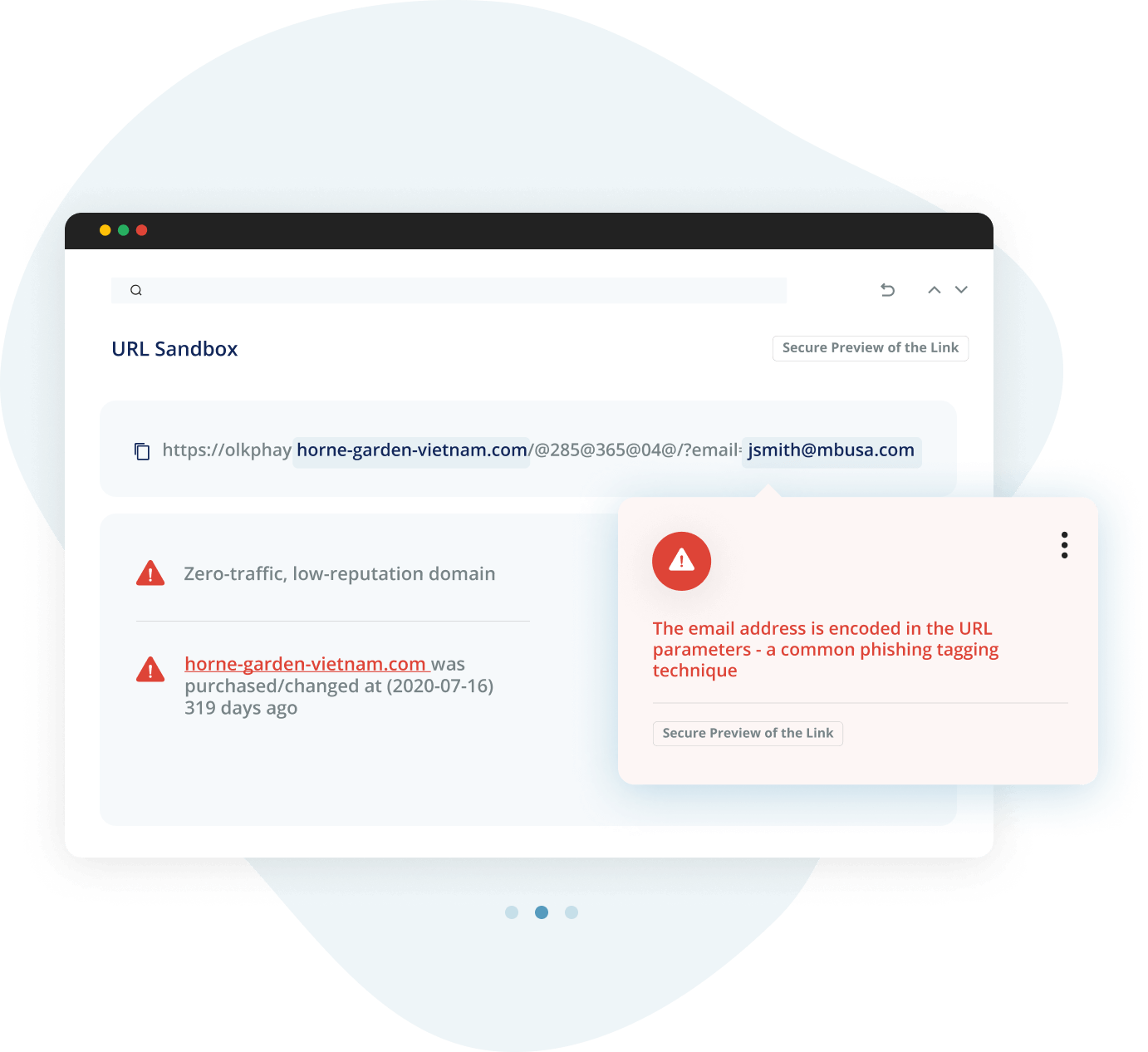
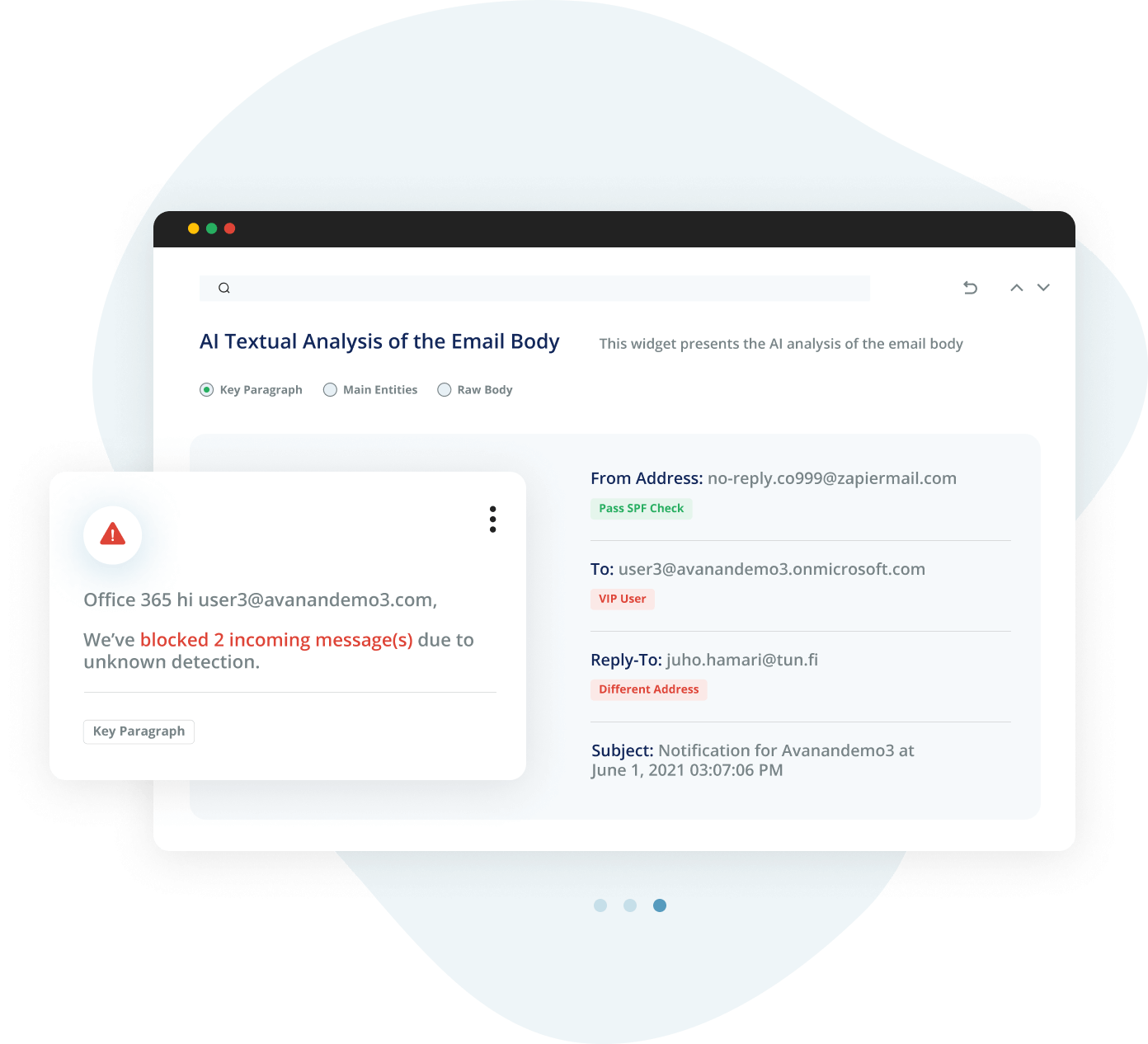
Avanan is powered by True AI, trained on comprehensive data sets to stop the most sophisticated phishing attacks before they reach the inbox.
Avanan uses advanced AI to prevent malicious
attacks from ever reaching your inbox.






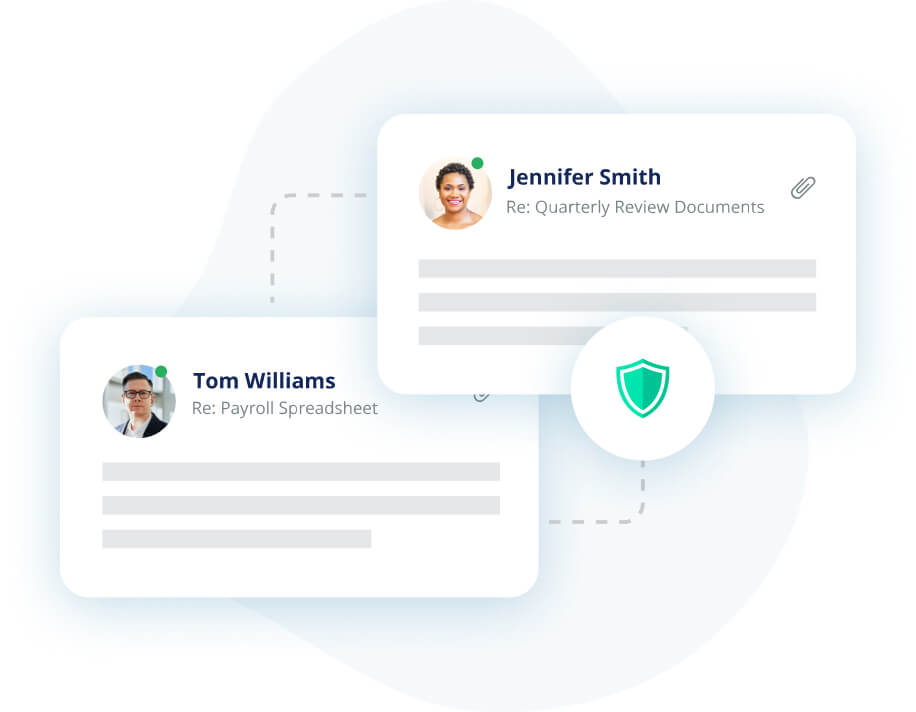
Avanan reinvented email security in 2015 because traditional gateways couldn’t—and haven’t—adjusted to the cloud. Avanan’s patented security:
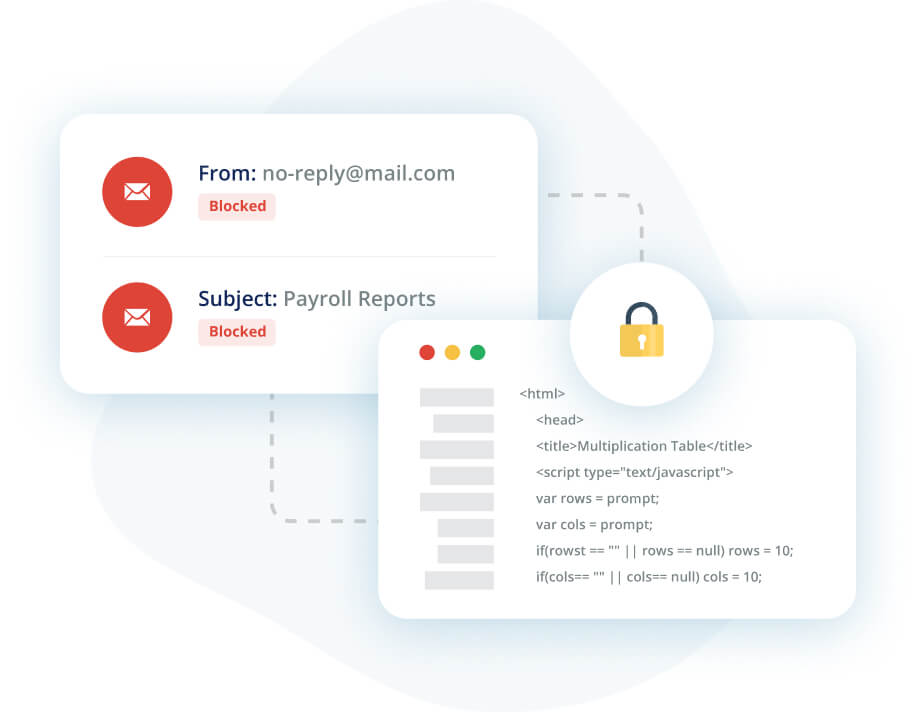
Default security misses far too many malicious emails, necessitating advanced email security to protect the enterprise.
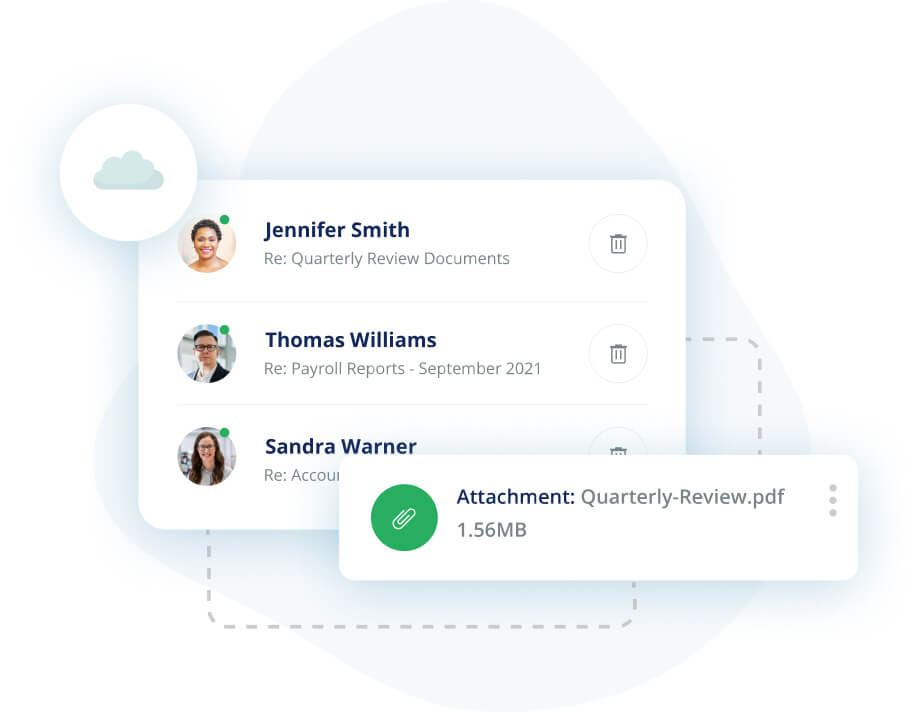
Cloud-native, AI and ML-powered solution that stops as many as 18x more malicious emails than SEGs.
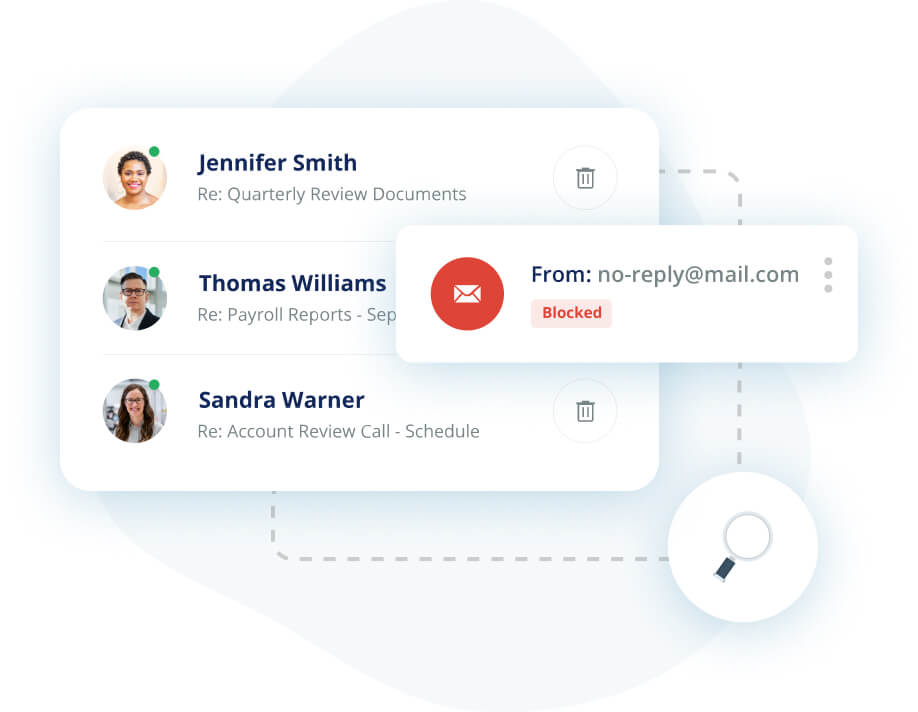
ATP/Defender has a high miss rate of targeted attacks, a high false-positive rate, and is difficult to configure and manage. Avanan catches the sophisticated attacks that ATP/Defender misses.
Our patented, inline solution blocks email before it reaches the inbox, scanning every message.



To implement API, machine learning and AI for cloud email security.
Ranked Email Security solution in Gartner Peer Insights and G2.
API-Based email security solution that can protect inline.
5,000+ customers, 60% coming from large enterprise.
Avanan is powered by True AI, trained on comprehensive data sets to stop the most sophisticated phishing attacks before they reach the inbox.
Caught a tremendous amount of threats that ATP and Zix SecureGateway left unchecked. Avanan has been our most reliable email security layer in our organization.
Visualization Engineer, Finance Industry
We selected Avanan over Email Laundry, Mimecast and Proofpoint. Their design is much more cutting edge and simpler to implement.
CTO, Retail Industry
Avanan has proven to be a better option than Microsoft ATP. Start directly with Avanan instead of ATP
Infrastructure and Operations, Communications Industry
We were receiving too many phishing emails. Avanan is stopping all of them.
Systems Integrator, Manufacturing Industry
The solution was extremely simple to implement and integrated into our current service offerings. We spent less than one day with the onboarding team and began to see results immediately.
Senior IT Administrator, Manufacturing Industry
Do a trial. It's easy to set-up and they will be able to immediately show you how they can improve your email security.
Manager of IT, Construction Industry
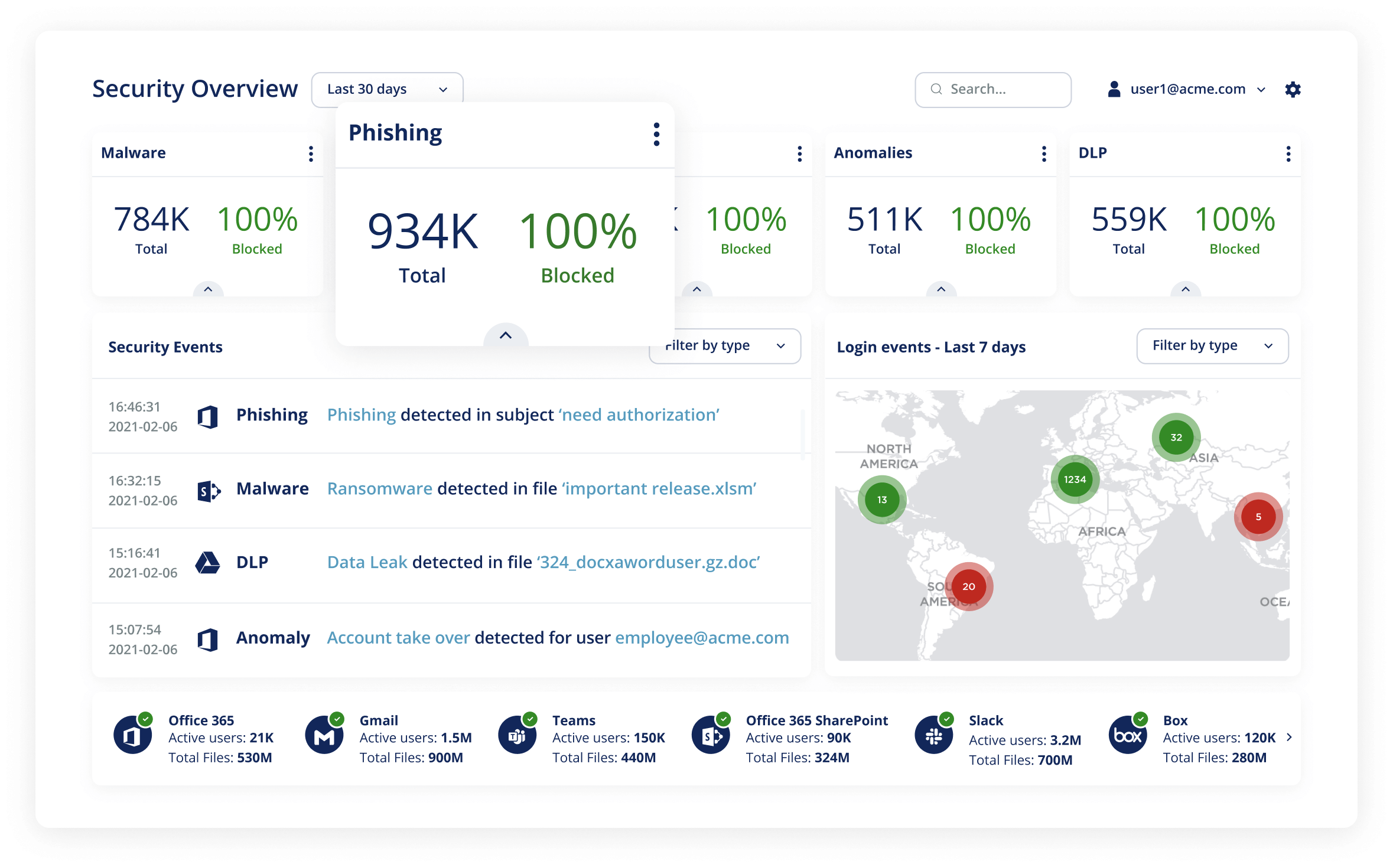
Avanan protects your email and collaboration suites from phishing, malware, ransomware, data leakage and much more
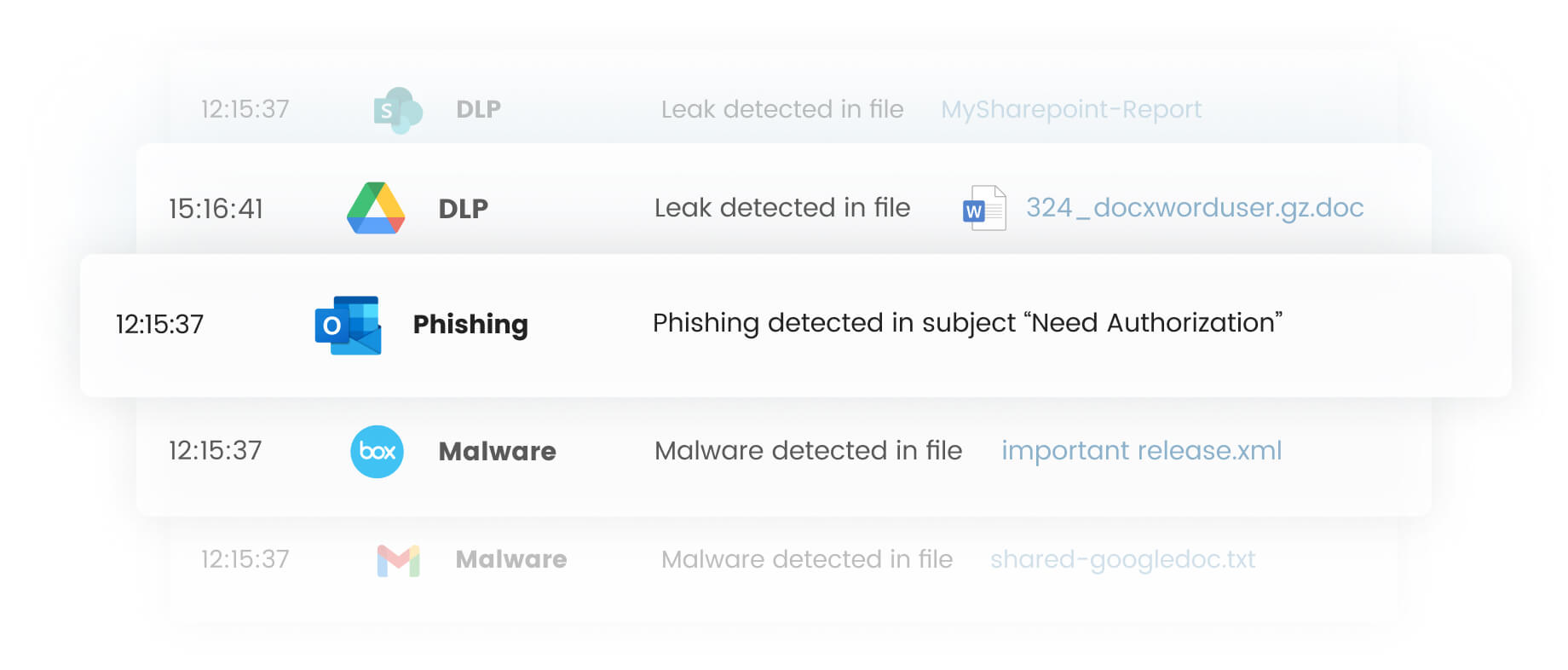
In today's rapidly evolving digital landscape, email remains a critical artery of communication for organizations worldwide. However, this [...]
As we navigate deeper into the digital age, the omnipresence of AI (Artificial Intelligence) in cybersecurity narratives has become [...]