Files that are behind direct download links are now emulated by the Check Point sandbox
Email cyberattacks are constantly becoming more complex and trying to find holes in security solutions. One of the manifestations of this improvement are attacks that involve links that – when clicked – initiate a file download.
These attacks manage to trick some prominent email security solutions, as they live in the delicate border between security engines designed to find malicious URLs and those that need to detect malware.
Avanan has been protecting from these attacks for years, using static analysis and the vast intelligence of Check Point ThreatCloud.
With this new release, the Anti-Malware (AKA sandbox, AKA Threat Emulation) is added to the mix to extend the protection against zero-day files that hide behind links.
Files behind links to direct file downloads will be emulated before being delivered to end users.
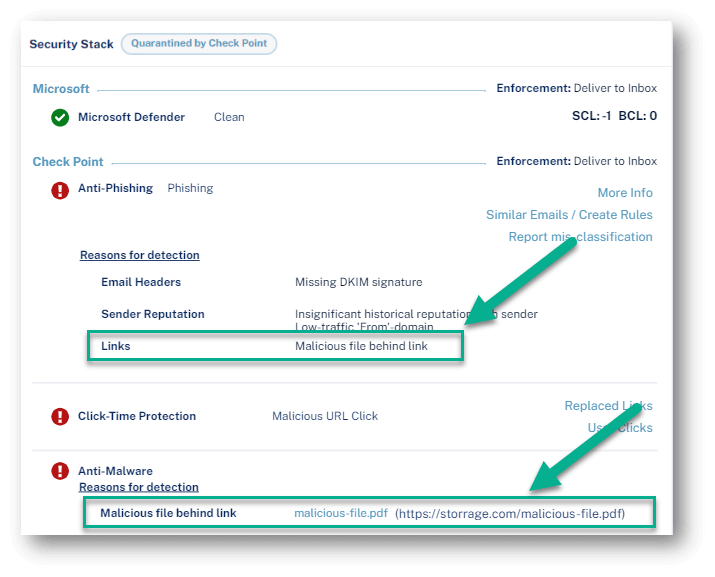
In addition, to prevent attacks in which the file behind the link is altered after the email is sent, this inspection will also take place when users click on such links after they are re-written by Click-Time Protection.
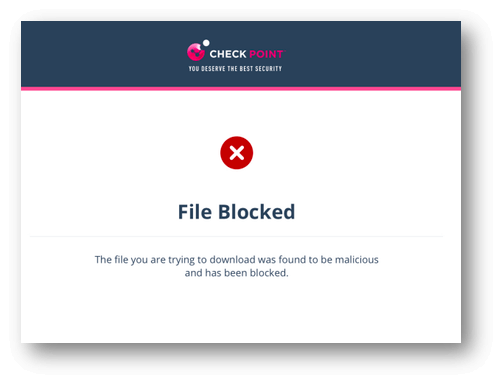
If the file behind the link is found to be malicious, access to the file will be blocked
Note – this feature is being deployed gradually. You should see it in your portal during the next 2 weeks.

