Version 2.6.0 will begin deployment for all customers on November 20, 2019 at 8:00am EDT. This document covers the changes from prior release (2.5.9).
Key New Features
Summary Card Personalization
The ability to hide/show cards (Shadow IT, DLP…) and save as a user preference.
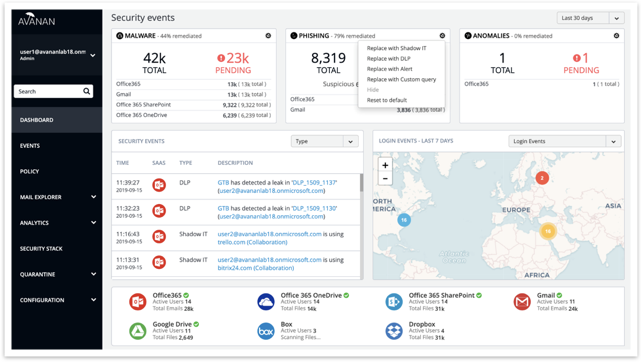
Dashboard Menu Changes
- Help button in left side menu, under login email address, for logging an Avanan Support ticket from the portal.
- Arrows for opening / closing sub-menus.
- Security Events filter (default per user).
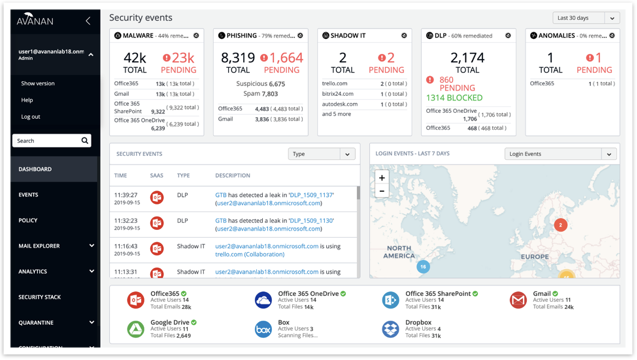
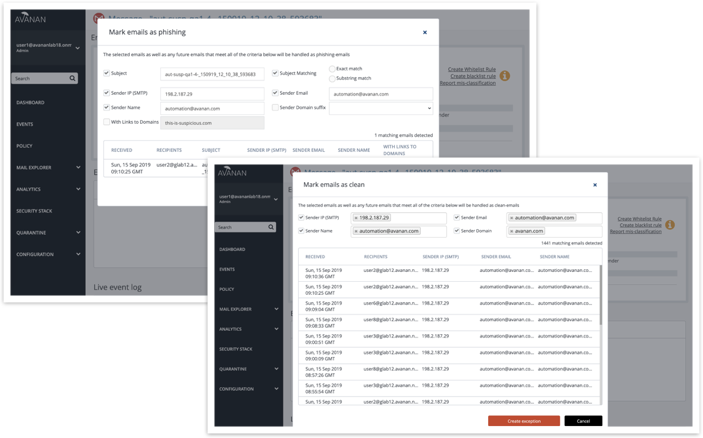
Anti-Phishing Allow List / Block List Enhancements
- Create Allow List / Block List rules directly from the email description.
- Show affected emails by selected criteria.
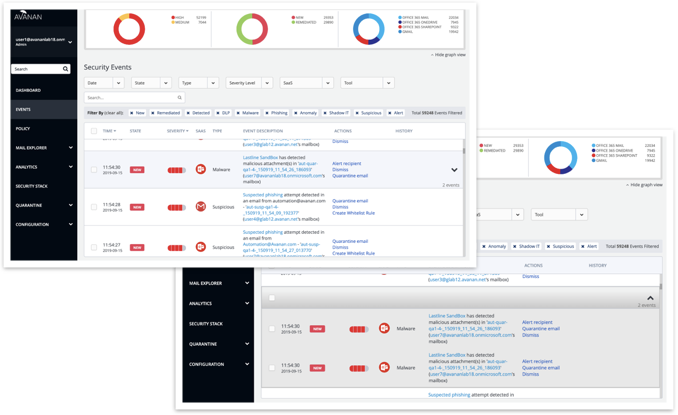
Security Events Grouping
When events are detected for multiple recipients, they are presented in a cumulative manner with group actions.
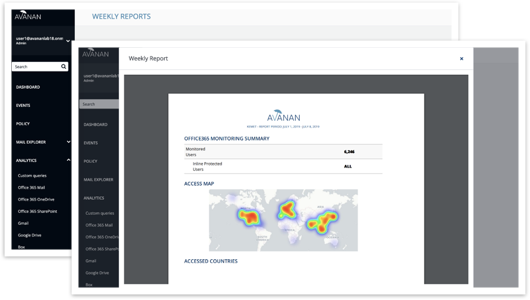
Weekly Reports Accessible From the Portal
Under “Analytics” in left side menu, Weekly Reports can be viewed, downloaded, and printed.
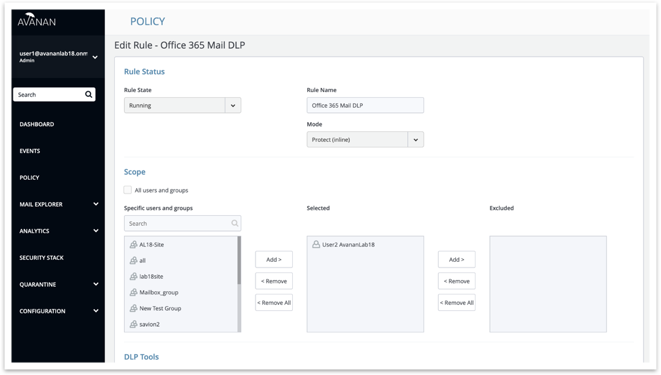
Policy Exclude Option
The ability to exclude specific users or groups from a policy.
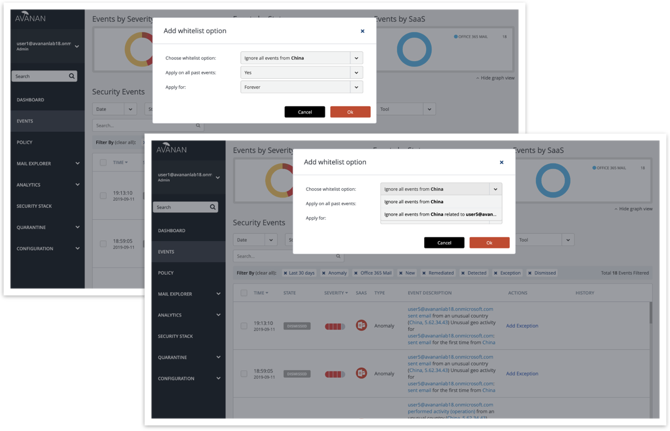
Anomalies Exceptions Management
The ability to add Allow List options (e.g. by country).
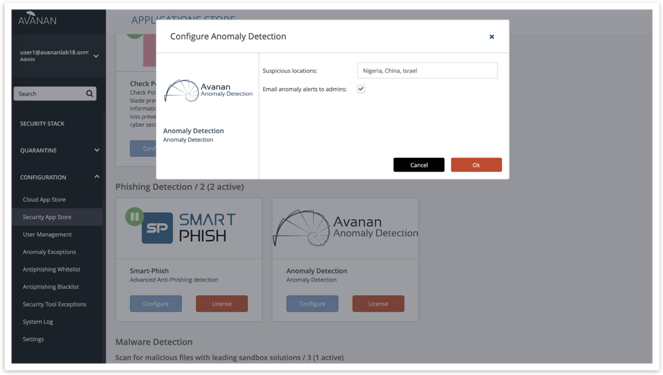
Configure Anomaly Detections
Under “Configuration → Security App Store,” anomaly configuration options can now be added (email alert action, Block List for suspicious geo-locations).
Note: anomaly email alerts to admins are now turned OFF by default and can be enabled here.
Encryption
Add “Encrypt” as a DLP detection action to enable third-party encryption. When configuring DLP, selecting the new remediation action ‘add-header’ allows for Avanan to detect outbound emails for data leakage and add an email header to it. The third-party encryption tool is activated using a mail flow rule that checks for the header and encrypts the outbound email.
Protection Against Executive Spoofing
Executive spoofing is a scam in which cybercriminals impersonate the names and emails of company executives to fool an internal employee into disclosing sensitive information or executing a payment.
In Avanan version 2.6, SmartPhish has a setting that allows Avanan administrators to automatically block such spoofing attempts.
Configuration
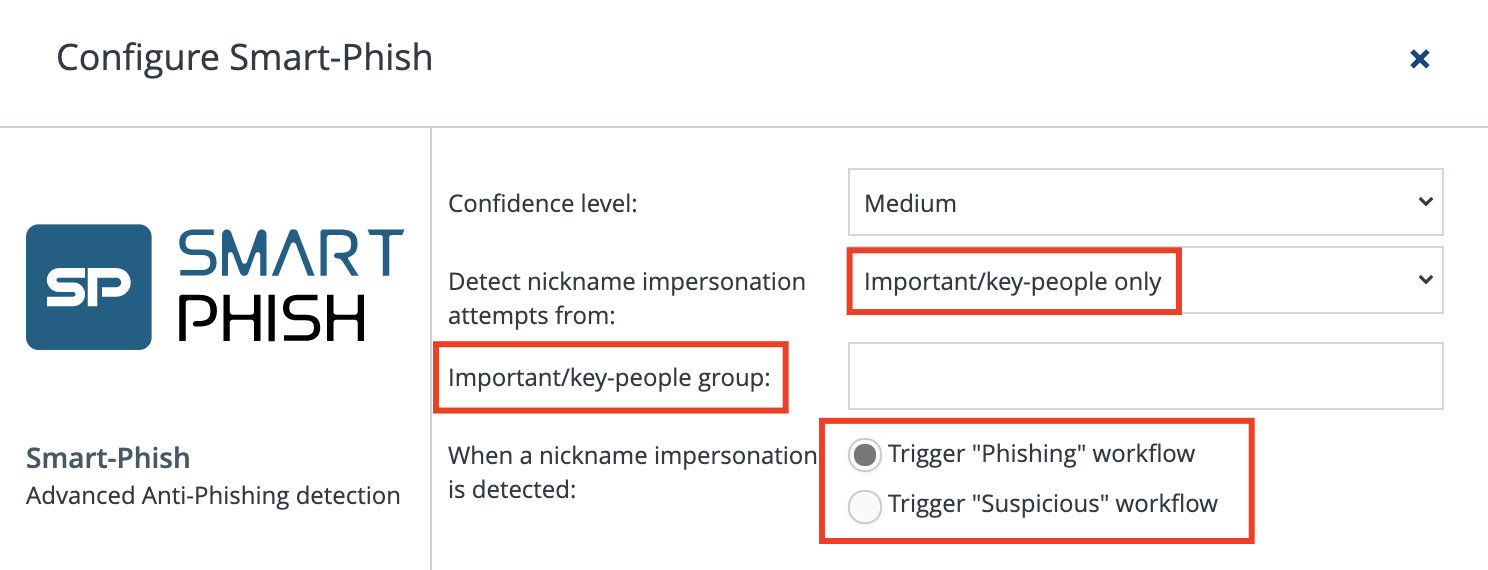
Avanan administrators can trigger their “Phishing” or “Suspicious” workflows when SmartPhish detects a nickname impersonation.
- Navigate to Configuration → Security App Store → SmartPhish → Configure
- Select the scope of users:
- Select the “Phishing” or “Suspicious” workflow for detections.
- Important/key people
- Note: By default, SmartPhish will reference the job title of the user to determine their seniority. (Examples of senior titles are CEO, CFO, CTO, etc.) Alternatively, you can define your own senior users by creating a security group (in Office 365 or Google) for senior-level users, and typing the exact name of the security group in the designated field in Avanan.
- All internal users
Best Practices
- It is best to start small. You can protect a small group of senior-level people and/or use the “Suspicious” workflow.
- If you wish to extend nickname impersonation workflows for all internal users, it is best to use the “Suspicious” workflow to avoid false positive detections (more below).
- Protected users must be informed to not use their personal email addresses, as these will be detected as impersonations.
Note that regardless of your settings, SmartPhish will always look for nickname impersonations for all users. The configuration described here will ensure that, for the scope of users selected, at least the “Suspicious” workflow is triggered.
Handling False Positives
Many commonly used services like Salesforce or ServiceNow send legitimate emails on behalf of other users. To SmartPhish, these will be detected as nickname impersonations. Therefore, it’s important to ensure that this configuration is not generating false positive phishing/suspicious detections.
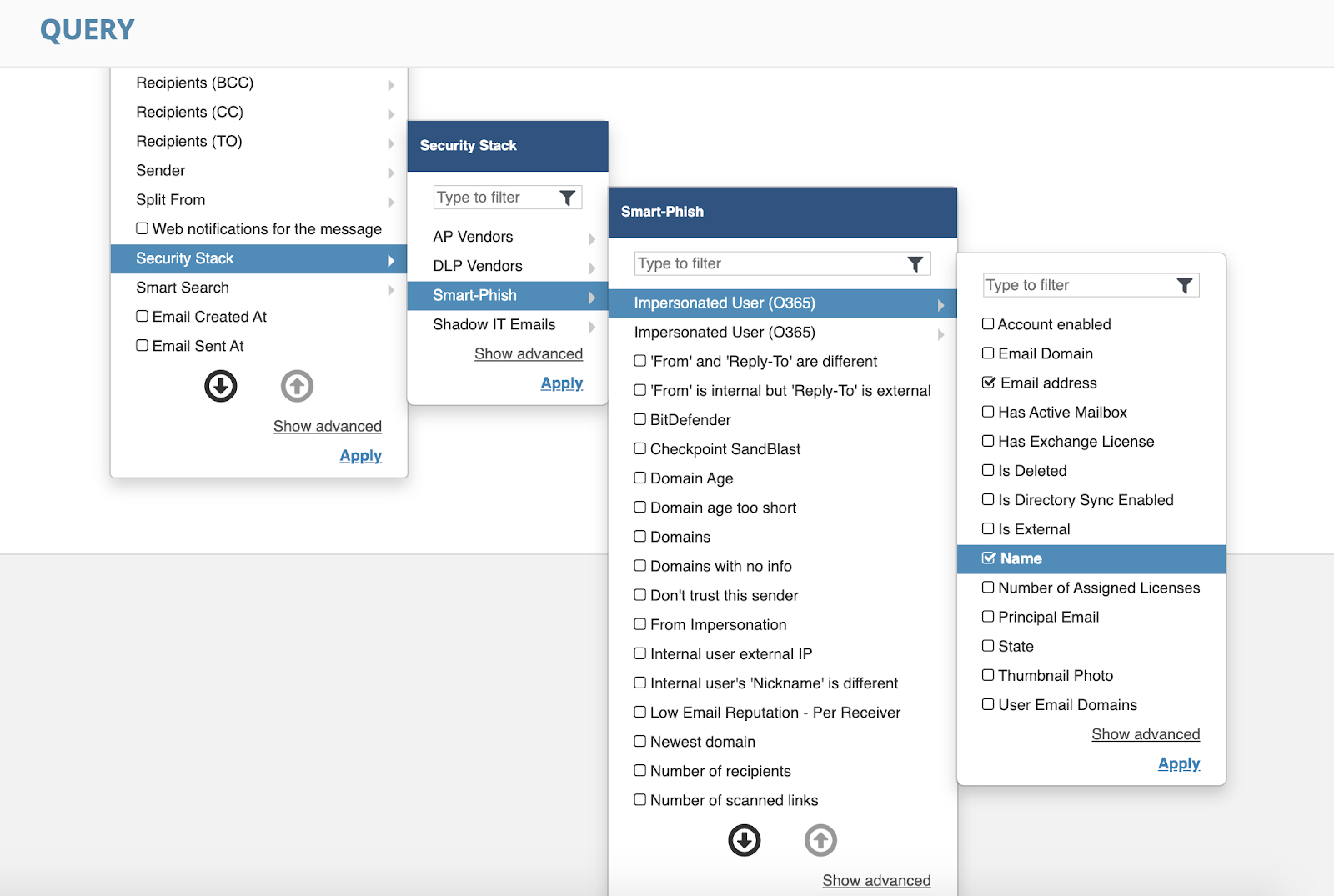
In order to do so, create a Custom Query that filters only for detections containing nickname impersonations. You can find the fields embedded under Security Stack → SmartPhish.
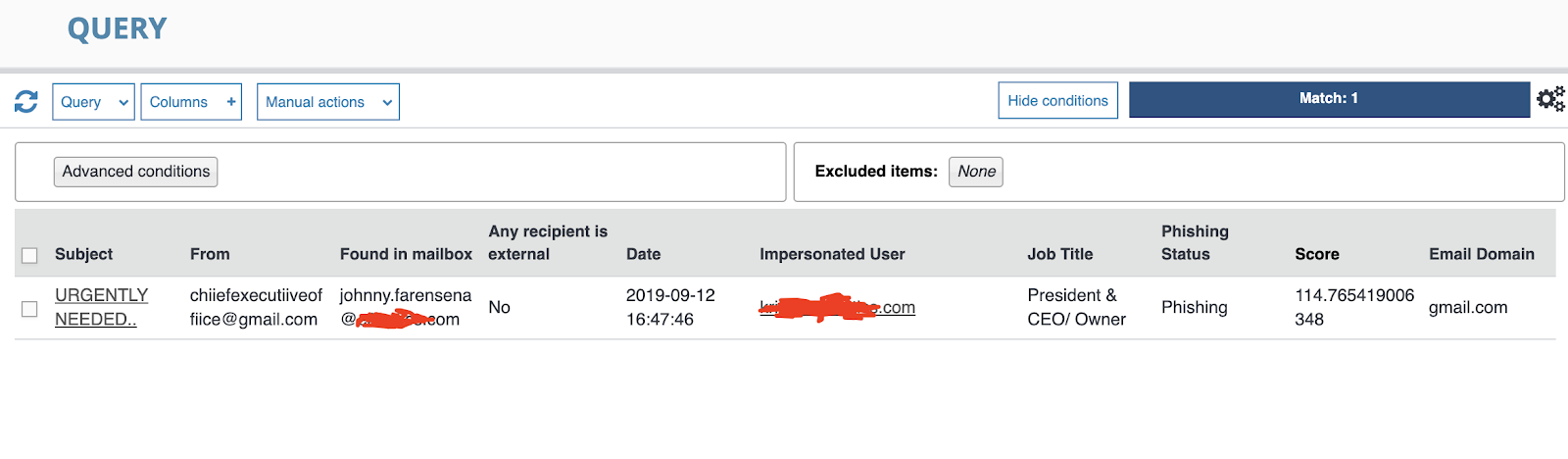
Example Output:
Be sure to Allow List legitimate services that appear in the query by navigating to Configuration → Antiphishing Allow List
If you have any questions or would like assistance configuring, please reach out to support@avanan.com.

