Recently, I analyzed the inboxes of a company representing a typical enterprise account of more than 10,000 email users. I found something alarming.
Because of Allow Listing configurations, 6.6% of the inboxes contained phishing emails that bypassed the email filters. These were malicious messages that would have been blocked if someone hadn't added the email addresses or, in some cases, entire domains to the Allow List.
When Allow Listed domains, senders, and IPs accumulate over the years, there can be unintended consequences on your phishing catch rate.
Why Allow List?
Most Allow List begin when someone finds an important email in the spam folder. By adding the sender’s email address or entire domain to the Allow List, every email will bypass the spam filter and go straight to the inbox.
Ideally, only the most trusted partners are Allow Listed, especially when typical communication might actually look a lot like spam. For example, a marketing group might send a lot of splashy clickbait messages. A finance department regularly sends and receives invoices and wire transfer requests that are often similar to malicious phishing attempts.
No matter why a company might add senders to an Allow List, the ultimate result is that all of these messages bypass email security filters.
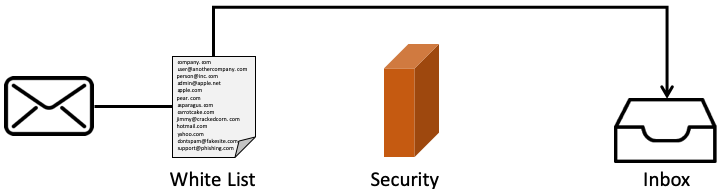
As these lists grow over time, they become ever-enlarging holes in email security. An ideal Allow List would consist only of individual email addresses, but it is more common to find entire domains. Worse, very few people document why they might have added something in the first place, making it difficult to remove items later.
Allow Listing in Gmail and Office 365
Five years ago, there was no choice but to rely on Allow Listing senders, domains, or IPs. Now, there are innovations that complement Allow Listing to protect the inbox. Powered by Artificial Intelligence (AI), the default and advanced security in Office 365 and Gmail makes intelligent decisions about messages with sensitive origins or content. Additionally, Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) identify authenticated senders, tackling the same problem as Allow Listing in a different way.
Office 365 and Google automatically Allow List their own services. That means for organizations using those clients, all internal traffic is removed from scrutiny. While this is a surefire way to present messages from trusted collaborators going to spam, compromised accounts will be much harder to isolate when the inevitable credential compromise occurs.
Interestingly, documentation for Office 365 and Gmail do not mention the word “Allow List.” Instead, Gmail has the approved sender list, and Office 365 has Safe Senders and Safe Domains. Although this might look like mere rebranding, it’s not. Microsoft clarifies that “EOP will honor your users' Safe Senders and Recipients, but not Safe Domains.” Websites are compromised all the time, and betting that a domain will remain safe indefinitely can be a dangerous assumption.
💡Microsoft Office 365 Allow List Configuration Tip
A domain-based list in a mail flow rule isn't as secure as an IP address-based list, because domains can be spoofed. Any messages sent from these IP addresses aren't checked by the content filter.Allow Listing tips
Combing through Allow Lists isn’t the most exciting way to spend time, but it must be done. Here are four ways to easily manage your Allow List:
- Allow List particular email addresses instead of domains. Allow Listing entire domains makes it easier for emails from spoofed sources to circumvent your security. Allow Listing specific senders, however, is much more manageable way to achieve a similar result.
- Don’t Allow List your organization’s domain. Hackers commonly spoof their target’s domain so that the recipient has their guard lowered. If they spoof the message and content well enough, it will fool your email security, too.
- Don’t Allow List mega-companies, like Amazon or PayPal. One of every 25 branded emails is phishing, making Allow Listing brands a risky endeavor. (Learn more stats in our 2019 Global Phish Report, and attend the web briefing on May 29.) Of the total number of brand impersonations Avanan observed in the wild, Amazon is the most frequently impersonated brand at 38%, right behind Microsoft. Allow Listing these globally-trusted brands makes hackers’ jobs much easier.
- Include thorough comments when adding items to the Allow List. This makes reviewing them in the future an easier task. Add why the item was Allow List, and when.
When it comes to security, every bit of content should be scrutinized. Generally, letting static rules pile up without review is problematic, creating technical debt that will cost time and resources down the line.