The Basics of the Nickname Email Spoof Attack
We have trained our users to distrust a sender's nickname and validate an identity by looking at the original email address. Most email clients will show both (a). Sometimes, you will get an email that does not have a nickname, so your email app will just show the email address in it place (b).
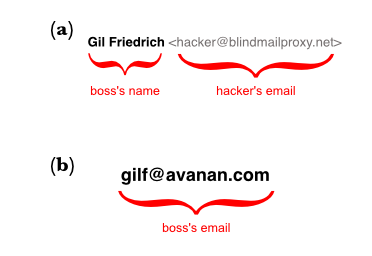
In this attack, the sender creates a nickname that looks like a friendly email address to hide their own. The problem is, that in the lastest version of Gmail's client (and within many phone apps), only the nickname will show.

Why is this interesting now?
Normally, Gmail shows the email address of every sender. Early in September, Google changed its internal rules to hide an email sender's address for certain messages. If you use Google, you can look through your inbox to see when it might have affected yours. It only affects some senders, based upon an algorithm within Gmail's filters.
Before the change:

After the change:

This change is normally a benign one and not universal. Google will only hide the email address in particular circumstances. The reason this is interesting is that only a couple of weeks after the change, we have begun to see phishing attacks that target this specific behavior and are able to trigger the hiding behavior.
Targeted, Automated, Sophisticated.
We see phishing attacks all the time, so new attacks are not news, but this one was interesting because of a combination of factors.
- It is only targeting Gmail Business users, as we are not seeing it across other accounts.
- It is automated, as we are seeing it simultaneously across multiple companies;
- It is a customized spear-phishing attack that uses account-level information, so it is relatively sophisticated.
Even though the problem has always existed with phone clients, we suspect the timing is due to the change in Gmail's behavior.
Spoofing the Email Nickname.
Like most phishing attacks, this version spoofs the nickname field to convince the target that it is from someone they know and trust.
Most users have been trained to second-guess the FROM field, especially when the email asks them to open a link, download a file or take some financial action. For example, if they see the name PayPal in the FROM field, they will look to find that it is actually from <hacker@somedomain.com>.
This attack precludes that action by actually displaying the the email address in the field in a way fools victims into believing they are seeing the actual email address and that the email address is someone they know within the company.
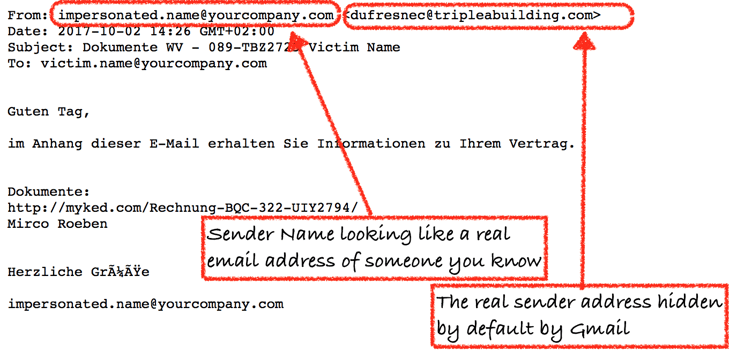
Here's a typical email - the hackers impersonate a real user by setting the sender name to be identical to an email address of someone in the organization.
Why this attack is concerning.
What alerted us to this attack is that it was able to take advantage of a recent change in Gmail's behavior and targeted only those companies that were using Gmail for their corporate email services. More importantly, each email was crafted so that the nickname seemed to be coming from someone within the target organization—a real 'company.com' address was used as a nickname when sending to a 'company.com' victim. This would be expected if the process were a manual one, with a human attacker crafting the message. In this case, the volume of emails seemed to indicate that the attacker had a large database of gmail addresses and automating the sending via a bot.
While this was easy to spot for our anti-phishing tools, they had bypassed Google's own filters and would easily fool even the most security-aware user.






