Emails with fake invoices has been one of the most popular attack vectors against Office 365 email users for the past several years. The malicious emails are disguised as invoices and sent to Office 365 users, commonly to the people in the organization that would approve these invoices. Every day, we are catching these attacks as they slip past Office 365's security scans.
The obvious questions that arise are:
- Why are they so common?
- Why isn’t Office 365 security catching them?
- And finally, what can you do to protect from it?
All of which we will be answering in this blog.
How Widespread is the Attack?
Among our customers using Office 365, we have seen this attack plague every customer, across hundreds of organizations. Many of our customers initially reach out to Avanan for our solutions after having fallen victim to such an attack and transferring funds to an attacker.
The reason this attack is so popular is that the monetization path for the hackers is obvious—they ask you for your money. Today, the hacker already knows with high likelihood who is approving the invoices in the company. This information is as readily available as a LinkedIn profile. They also know with high-likelihood what services the company is using, and what invoices for those services would look like.
In summary, the hacker crafts a fake email that goes to the right person in the company and looks completely genuine. This is why success rates for this brand of phishing attacks is high.
With a clear monetization scheme and high success rates, it is no surprise this is such a highly utilized attack strategy.
Why Are These Fake Invoices Bypassing Microsoft Security?
False Positives
The reason this attack is so challenging is that there are actually a lot of legitimate invoices being sent via emails, either from specific people or from automated systems that the company deploys. The legitimate emails can have the invoice as an attachment, but nowadays, more commonly includes a link to view the attachment online.
The challenge for Microsoft is that the legitimate emails come in so many shapes and forms, and the hackers are using that to their advantage.
Zero Day Links
The other challenge is that for links Microsoft relies heavily on Block Lists. But in this cat-and-mouse chase, hackers turn to zero-day links that bypass their link scanning tools. For a particular site to be added to a Block List it has to have been used for a long enough time period to be considered a threat that will be seen again. Microsoft can't simply Block List a site because it has never seen it before, as this would result in too many false positives; the newness of a site does not necessarily mean it is malicious. The attack is creating and using new sites for each attack as a way to stay ahead of any Block List rules. This isn't just Microsoft that will have trouble detecting the link. After testing multiple link reputation tools, we could not find any one of them that detected the invoice URLs as malicious at the time the email arrived, or even within 1 hour after.
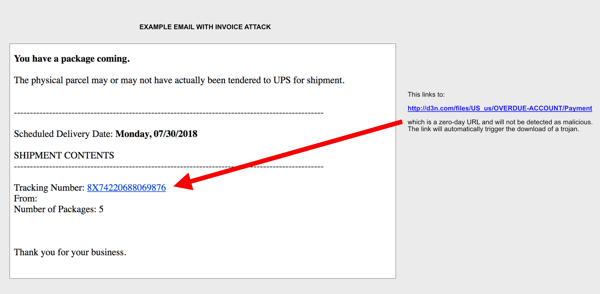
User Impersonation
Finally, in many cases, the invoice fakes an automated invoicing platform. But in some cases, we have seen attacks that appear to come from a person. In one version, hackers used the “CFO Impersonation” attack, where the email arrives from someone who appears internal (like the CFO) and is ‘forwarding’ a fake invoice to an employee who is expected to process it, with a short “approved” or “please process” message. In other cases, a compromised Office 365 of a partner is used to send an invoice to the company they work with, as a method to monetize compromised accounts.
How Can It Be Detected?
Clearly, relying on link reputation for security just does not work. Instead, Avanan’s machine-learning looks inside the email metadata and context. By looking at historical email correspondence and contextual clues in the email that point to it not being a real or expected invoice, Avanan has been able to detect and block this attack despite the zero-day nature of the URL.
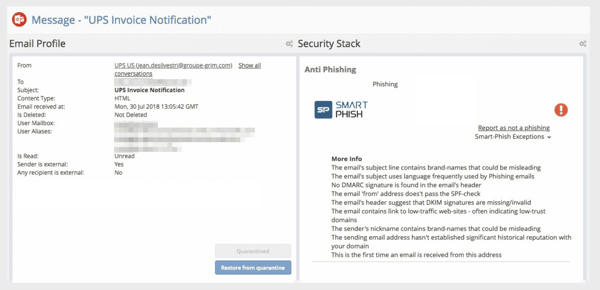 screenshot showing criteria which lead to Avanan flagging an invoice phishing attack
screenshot showing criteria which lead to Avanan flagging an invoice phishing attack
These indicators will also look for impersonation attempts of the sender name or brand names and will compare them with a vast database of how an invoice from this organization would be expected to look. The natural language analysis marks those emails as request for payment, that when correlated with sender’s traffic history, marks those emails as suspicious or malicious, and either blocks them or warns the end-user, depending on the policy you configure.





