In several past blogs, we described how hackers bypass Office 365 Security with Punycode encoding, and then Unicode characters.
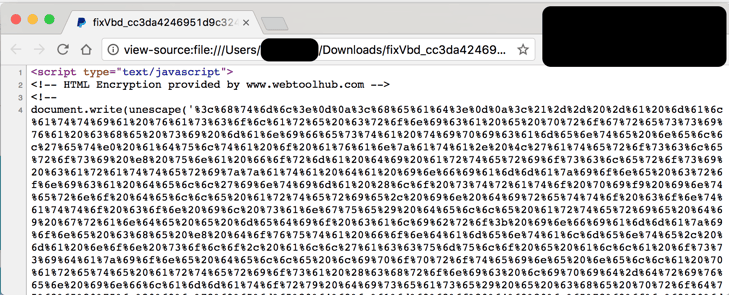
In this attack report we discuss an attack against Office 365 users that is quite unique and leverages another type of character encoding called "Hexadecimal Escape Characters". The attack has an HTML attachment with a javascript snippet, and the content is encoded through hexadecimal escape characters, therefore no links are visible, but when opened, it presents a locally-generated phishing page with login instructions.
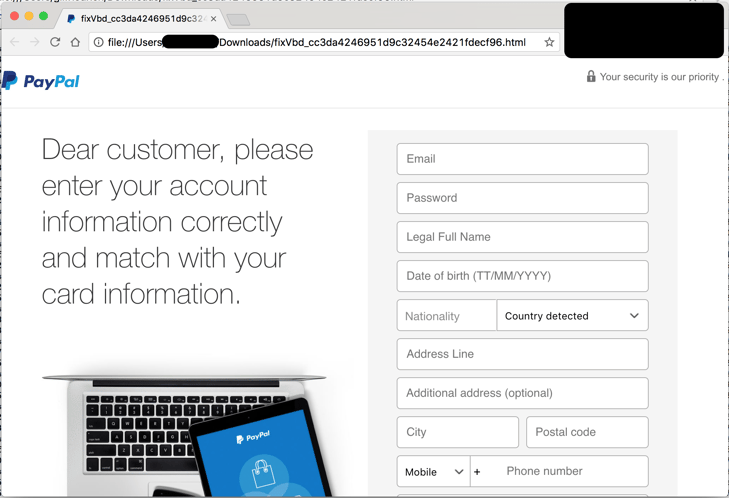
Here's one example that we've seen in several instances: a fake paypal.com email that, when rendered, displays a forged Paypal login.
and here's the javascript and how it's obscured in hexadecimal escape characters:
How it works:
Pretty simple - you get a message, let's say from Paypal, and you click on what looks like a link, but is actually a local file. The 'link' (attachment) then opens the Paypal login page that you would have expected. Sophisticated users would see the top bar starting with 'file' and not 'https' but many won't notice. Once you put in your credentials, the submit button sends the information to the hackers. The page and its form is rendered locally so that nothing is sent or received until you click 'submit'.
How is this attack passing your security?
There are several factors in this attack that make it unique, allowing it to bypass most security tools– including Microsoft's Office 365 default security–but also some other more advanced sandboxing technologies including Microsoft's Advance Threat Protection:
1. Scanning this file with most antiviruses and emulating the file in a number of sandboxes (including Microsoft's ATP) failed to find it as malicious. This is because it has no known signature, and no active content (macro etc). It also has no apparent links - those are obscured and not easy to extract.
2. Even when rendered in Microsoft's ATP or other sandbox, it may expose the links, but most sandboxing technologies do not follow those links. They just don't consider an HTML file with a form and a submit button as malicious. It is not considered 'active' code. As a result, the attachment is not found to be malicious when scanned.
3. The email body itself has no links (as the link is in the attachment) - therefore, any of the 'safe-link' methods (replacing the URLs with proxy-links) that Microsoft and other email security vendors like Proofpoint or Mimecast are rendered useless.
4. The fake "login" screen is local. Firewalls or browser plugins that use URL reputation for IPs and domains are completely blind to this because it isn't going to the internet to fetch the page, it is local. Same applies to any DNS based security, like OpenDNS from Cisco and similar tools.
What can you do?
Avanan's anti-phishing machine learning algorithm detected this attack based on several factors. Factors like domain impersonation (in our example, 'Paypal'), together with sender email address, sender-receiver email history, and more allowed the Avanan anti-phishing machine learning to flag this as an attack and block it.
Avanan leverages over 200 indicators ('features' in the words of data analysts) from multiple vendors to conclude if an email is a phishing attack. This is what allows us to catch the attacks that are missed by Office 365 and the email security vendors. Our novel algorithm is deployed as an app within the Office 365 app store. Contact us today and in 5 minutes and we will scan your company's inboxes at no cost for the phishing attacks that are there right now.







